In some cases, a spyware prevention message may appear on your computer. There can be many reasons for this problem.
Approved: Fortect
Use reliable antivirus software applications with anti-spyware capabilities.Don’t download suspicious attachments from email messages.Don’t click on pop-ups on the Internet.Do not open links received in text messages from unknown numbers.Don’t read messaging apps with strangers.
Spyware is another type of malware that monitors your online activity and determines sensitive policies such as credit card numbers or age. In most cases, spyware runs in the background of the device, invisible to those who don’t know.
How Do I Install Spyware On Your Computer?
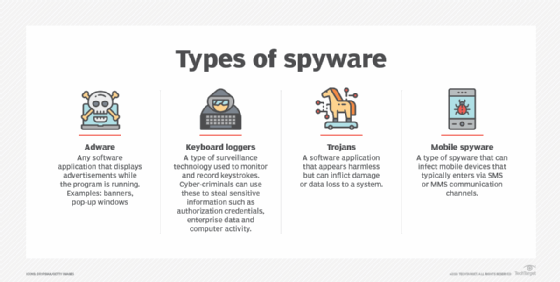
Spyware is a wide variety of programs that hide the background of your computer. Spyware can use several methods on this device, including:
- An attacker has installed spyware on your device.
- Downloading software or content from another infected source.
- Open sub visual emails
- About insecure internet connections
How Does Spyware Work?
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

Spyware privately tracks cookies to map your usage of the globe, tracks your social media activity , sends out emails you send, and more. It is often used to personally promote oneself for the purpose of selling to third parties such as publishers. It is also used as a method that remains hidden from others and uses someone else’s actions in the interests of the hacker.
Examples Of Real Spyware
A common spyware scheme is to use special keyloggers or tools that register a public type, or tools that take screenshots associated with your device.
For example, log into your favorite online store and start shopping. In the background, you don’t know that the purchase is usually intercepted in a screenshot that is usually sent to attackers. Unfortunately Now your attacker can find out your real credit card number.
Spyware can look like this: a pop-up window telling you that your computer’s time should be turned off, another one claiming to be a spyware warning, or even a regular file download window that suddenly pops up that you don’t know about … You weren’t expecting. In this example, it appears as a pop-up warning about a computer virus.
Spyware: A Brief History
The term “spyware” was first used in October 1996 and appeared on Usenet. A few years later, the term was also used to refer to spy devices such as controlled cameras inside devices . It was in 1999, when the term became generally accepted, and in 3000, perhaps the first anti-spyware application was released.
From 2000 to today, attackers have only been more ruthless in their ability to gain access to our personal information. However, spyware vendors such as Norton and McAfee must be just as ruthless and constantly develop new office tools to help us stay safe.
• »¿How Do You Want To Protect Yourself From Spyware
You have the ability to come into contact with serious malware every time you use your devices. It is important to understand the simple method for blocking spyware when browsing the web, cleaning up your mailbox, and more.
-
Use anti-spyware. Software is the front line between you and the attacker. Antivirus has several features to suit every budget and need.
-
Update your system. Be sure to update your browser and your device as a whole. There may be a bug that keeps your company’s device open to spyware that can only be fixed with a recent update.
-
Be careful when you need your downloads. Be careful when downloading content from file sharing websites . Spyware and / or spyware h It hides these downloads.
-
Avoid pop-ups. As tempting as they are, don’t choose to have pop-ups appear on your screen. You can also install a Popup Blocker and never interfere with its operation.
-
Keep track of your email. Do not upload documents from unfamiliar email address . Better yet, don’t open emails. Delete them.
Some of the most common reasons why attackers can use malware is collecting data for disclosure to third parties, stealing someone’s identity, or spying on the use of their computer.

While spyware, along with malware, can be one of the most common ways to infect your device, you can prevent .
following these tips
Speed up your computer's performance now with this simple download.

