Approved: Fortect
Recently, some users reported that they came across a malware security guide.
A security tool, if not a familiar security tool, is a villainAnti-spyware technology from the same family as the system Security . This is facilitated by the appearance of Trojans and pop-ups.If this criminal is announced through a Trojan horse, it will most likely be installed on your computer.without your license or knowledge. If you are advertised through pop-ups, youWhen you are online, a pop-up window will appear indicating that your computer is frequently infected.Clicking on the popup will take someone to the home page that displays the ad.claiming to be a fantastic fake online anti-malware scanner. At the top of the adHe indicates that these are usually infections, and then prompts you to download andInstall a security tool and to your computer.
After installation, the program will remain configured to start automatically.when you log in from your computer. Once launched, it will probably perform a scan, and if soWhen you’re done, point out that most of them are infections on your laptop or desktop. if you areTry to remove these infections, in fact it is not allowed except for the firstBuy the program. The reality is that the scan results are scams, just likethe infected files that should be on your computer are actually legitimate windowsFiles. With this guide, you will hardly have to manually delete any of the files listed in it.are infections that can affect the proper functioning of your computer.
When the program is running, you will see many warnings on your current desktop.and from the Windows taskbar. This information indicates that your computerencountered the Security Tool Firewall malware stopping the program,or that an active charge has been detected Attack by malware. Text some ofYou can see the following warnings:

Security Warning
Spyware.IEMonster activity detected.These are attempts by spyware and adware, passwords for Internet Explorer, Mozilla. stealFirefox, Outlook and other programs.
Next to it, click “Remove immediately with SecurityTool”.
and
Security warning
Some important system files on your computerhave been maliciously modified by programs. This can lead to system instability.Loss and.
Click below to block unauthorized changes by removing risks (recommended)
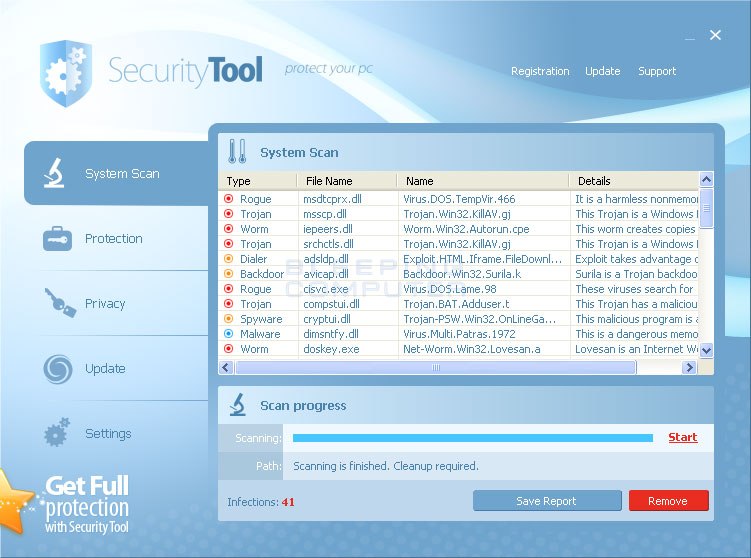
Like the scan results, these safety instructions are not genuine andare shown directly to scare you when you dream that you are infected. the largestThe problem with this drug is that it won’t allow the program to run.other than the people required by your operating system. When we try to startthe program when the security tool is launched, whichEach of our programs and states stopsthat he is infected. In fact, there is nothing wrong with most programs andInstead, the security tool preserves your robust ability to run ransomware until you do.Buy it. Fortunately, we have a way to get around these limitations with thisYou can get your computer repaired without paying the ransom.
If someone is infected with a security tool, take a moment and use the removal guide below.from your computer for free. If you have already purchased the program, thenwe recommend experts who say to contact your credit card company and also dispute expenses.because this program is a big scam.
Security Removal Options
Self Help
This tutorial contains detailed information, but it was recently written and everyone will follow. Make sure the actual data is saved before proceeding.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

If you are uncomfortable incarry any changes to this computer or follow these steps, don’t worry! Instead, you can get free personalized help by asking a question in the forums.
- Print, plus these instructions if you need to close each windowwill open later as part of the fix.
- Restart your computer to switch to online mode. TOdo this, shut down your new computer, then on the fly again, and when youWhen you see something on the LCD, press the F8 key on yours.Keyboard. Finally, you will be taken to a menu similar to the following:
Use all the arrow keys on your keyboard to select Safe with Online Mode.and press Enter on your personal keyboard. If you have any problemsswitch to safer mode, then follow the sequence: Commentto start Windows in safe mode
Windows will now boot into Protected Mode with Networking and ask you to connectas a user. Please login as a user withwith which you are previously logged inin normal Windows mode. Then move on to the rest of the steps.
- The infection that you usually try to remove may prevent this from happening.Download files to the infected computer. When you find that it isIf you follow these instructions, you will need to download the requestedThe files in this guide are to help another computer, and then transfer them to the infected computer.A computer. You can transfer files partially via CD / DVD, external drive or USBUSB key.
- Before you can do anything, you must first kill the processes you encounter.Security toolso that it does not interfere with the cleaning process. Please do itDownload RKill to your desktop from the link below.
RKillDownload link page (download may open in a new tab or new visitor window.)
On the download page, click the Download iExplore Now button.Label.exe download Associate. When asked to do thiswhere you want to save the product, save it to your desktop.
- Splitbut infection can hide the Windows desktop, some of us have to open a window with a resolutionthat we can see the symbols.
If you are using Windows XP, follow these steps:
Click the Start button, then just click theExecute the menu item. When our launch window opens, enter% UserProfile% desktop. aEnter this keyboard in the “Open”: field and click “On”.
If you are using Windows Vista, or perhaps even Windows 7, follow these steps.
Click the Start button and type% UserProfile% desktop. aOften the menu type starts with the search box below. SoClick On to enter your PC keyboard.
- You should now see a window showing all the icons on the desktop, includingiExplore.exe program. Now double click the icon associated with iExplore.exe.Icon To automatically attempt to stop all related processeswithSecurity tooland other fraudulent programs. Please wait while the plan looks differentMalicious software for programs and stops their work. When it’s over, it’ll be black asszhkaclose automatically and you can go to next stepNews that RKill is an infection, don’t worry. This message is onlyfalse warning fromSecurity toolWhen the program ends, you can delete it. If you did it inthese infection alerts that close RKill is a trick to get out of a specific alerton the screen, then run RKill again. from
Speed up your computer's performance now with this simple download.

