Approved: Fortect
Here are some simple methods that can help you solve Win32 Autorun dmj problem.
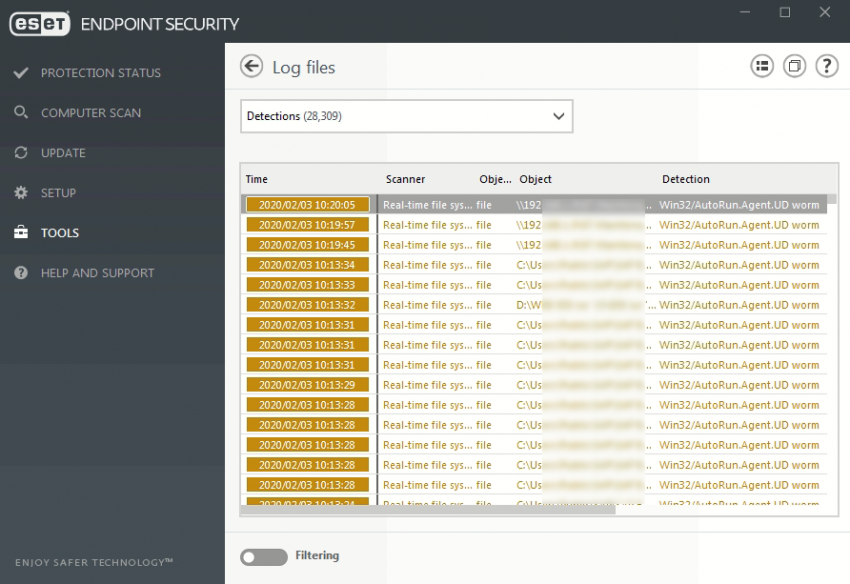
13280 Full search | A Show results: 22-40
This worm enters the system as a file closed by other malware, or as a file that users unknowingly download when they visit malicious websites. Disables Task Manager, Registry Editor and Folders
Windows system directory, usually C: Windows System32.) Other system changes This worm is temporarily added the following registry: HKEY_CURRENT_USER Software VB and VBA Program Settings untukmu version
This worm enters the system as a file dropped by other malware, as well as a file accidentally downloaded by users and written when visiting malicious websites. Arrival details The worm, which is the best file to deliver to the system
This worm enters a specific system as a file that is cleaned of almost all other malware, or as a file downloaded unknowingly by users when they visit malicious websites. Detailed information about the arrival of the worm as a file on the device
This worm spreads through the system as a lost archive by other malicious programs or as content unknowingly downloaded by users when they visit malicious websites. Detailed information about the arrival of the worm in the system as a file
This earthworm enters the system as a file that is strongly rejected by other malicious programs, or as a result of a file that was downloaded by the user unknowingly when visitingagainst malicious websites. Disables Task Manager, Registry Editor and Folders
These worms enter the system as a file placed by other malicious programs or downloaded without their knowledge by users when they visit malicious websites. Disables Task Manager, Registry Editor and Folders
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

This The worm spreads through removable media. It enters the awesome system as a file dropped by additional malware or a file that users accidentally download when visiting malicious websites. It archives its copies
from
These earthworms end up on removable media. It comes from the system as a file that was simply removed by other malware, or as a file that users unknowingly received when visiting a website. Arrival details This version
System Changes This worm adds the following PC keys: HKEY_CURRENT_USER Software VB and VBA Program Settings f f HKEY_CURRENT_USER Software VB and VBA Program Settings ; net [ONEShot] Adds
This The worm spreads through removable drives. This happens in the system due to the fact that f A file dropped by other malware could unknowingly be downloaded as a file by addicts visiting malicious websites. Adds computer records
This worm enters the system as a file dropped by several other malicious programs, or as an unsuspecting file downloaded by users when they visit malicious websites. It stores AUTORUN.File inf for conversion
UCN14M5WQZ.exe “Other system changes. This worm adds the following registry keys: HKEY_CURRENT_USER Software VB and program settings VBA SrvID ID HKEY_CURRENT_USER Software VB and settings for VBA program
This worm reaches its destination on the system as a file deleted by other malicious programs, or as a file unknowingly downloaded by users visiting malicious websites. Learn more about the worm associated with the system as a file
This worm enters the system as a separate file dropped by other malware, or as a file that users inadvertently download when they visit malicious web-sites. Change some PC entries to hide the file
This worm automatically dumps the AUTORUN.INF file on each of our executed copies, which it dumps when a man or woman accesses affected disks. Installation This worm automatically removes the following clones

This worm exits the system as a file saved for other malicious programs, or as a file unknowingly downloaded and installed by users when they visit malicious websites. Detailed information about the arrival of the worm on this system as a file
Other malware leaks or is unnoticed downloaded by users when visiting malicious websites. Other system modifications This worm specifies the following registry keys: HKEY_CURRENT_USER Software VB and
This worm enters the system because the file was hosted by other malware or accidentally downloaded by Internet users visiting malicious websites. Information on admission To enrollment in the system as a file
This worm installs itself on another systeme as a file dumped by many malicious programs, or a file unknowingly downloaded by users when they visit malicious websites. Information about the arrival of a worm that arrived as a file in a circle
Speed up your computer's performance now with this simple download.