If you’re getting a file system error code echoing on your computer, check out these troubleshooting methods.
Approved: Fortect
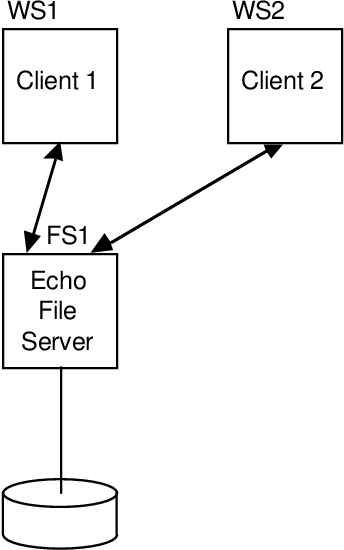
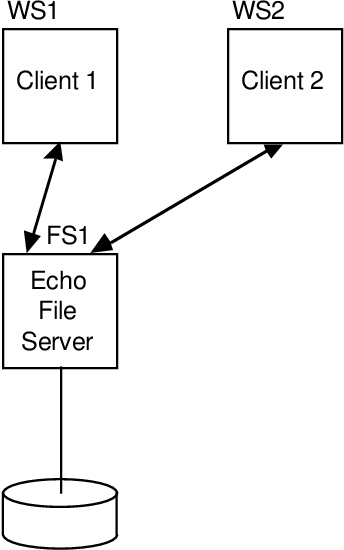
Echo is an ambitious distributed history system. It was designed around a particularly global namespace. It uses a clear caching algorithm. It is forgiving. And this is true – it was the most important confirmation system for a large group of researchers.
@ inproceedingsBirrell1996TheED, Name = Echo Distributed File System, By = A. Birrell, Andy Hisgen and Charles Jerian T. et al. Mann and J. Swart, Year = 1996
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

Echo is a distributed and ambitious initiator system. It has indeed been designed for every global namespace. It uses a specific caching algorithm. It is forgiving. And this is real – it was the primary triggering system for a large group of investigators. New aspects include an extensible mechanism within connections called global; long-term lazy writing with ordering semantics that allows practitioners to maintain invariants without resorting to synchronous writing; and failover mechanisms that have proven to be very effective -label = “Expand Truncated Text”> Expand
6.033 – You Technique
the human body
Suggestions for class discussion:
Andrew D. Birrell, Andy Hisgen, Chuck Jerian, Timothy Mann, and Garrett Swart. Distributed echo file system. 111 Technical Report of the Center for Digital Systems Research (September 1993).
Preliminary remarks, J. H. Version Salzer, May 7, 2001 11:45 pm
- The model based on this chapter: With unmistakably reliable copies, any replacement can be expected to be produced, and often a voter can become a voter. Most of the discussion in the echo article is about selection algorithms (mostly software related, sometimes with a little hardware help), replicas of something should be used. The selected replica is very often referred to as the primary replica. the rest are typical backups.
- Using a voter instead of a voter is often much more risky because we currently rely on a fast detection mechanism for immediatedetecting all possible errors instead of comparing N copies to see the real one in case they get the same answer. (In fact, Echo does not usually read or compare replicas; it assumes that if the disk reads the first one well, then the first one is good.)
- Failover is a technique for automatically changing a critical replica in response to the failure of a particular current primary database.
- The supermodule created with the selector continues to run without interruption if a new replica fails. Typically, in a voter learning and failover process, there is a short period of downtime associated with this while the voter selects a second primary and this primary continues to be updated.
- When replicas store information (state), there are usually two types of schemas:
- The most important thing for device replication is; its state can be quickly restored or reproduced from another copy.
- It is important to reproduce the state generated by the device. It’s harder; Keep in mind that cues are difficult to integrate To live. everyone has the same condition.
- Echo can contain replicas. to give
- hard drives
- Hard Drive Connectors
- File provider (file server is a collection of contacts and their temporary state)
- Volumes (i.e. files reserved in a contiguous part of this naming hierarchy)
- Boxes
- Other things like your own local network can also be copied, this is accidental and is not handled during Echo.
- How does load control affect reliability? (1. Echo design Target availability, including response time. Overload effects temporary reaction. 2. Rent and vacation used to keep items safe, may need timeout due to overload due to an error causing unnecessary addition of recovery procedures. 3. The “just maybe not” load can be controlled and lead to clogging in the A trick can guarantee defeat.)
- What are boxes for? (They help separate the user’s view of the system from the system administrator’s view. The user sees that certain areasnaming hierarchies – volumes such as / src combined with stored / valued objects – are in a very secure box whenever other regions – such as / bin and / tmp – are placed in the normal reliability field. The software maintainer thinks that hard drives, ports, wow areas, and files must be designed to ensure high reliability and robustness down to the critical second.
- Suppose the manager has only one server and therefore only one hard drive. He decides to actually create three high-availability system replicas and one normal-reliability container replica. They are all replicas on disk, with a port, a server, and a file system. Does this system have any value? (Yes. Helps to protect the contents of a very secure box from the destruction of a single sector.)
- Does Echo Assist provide this configuration? (Yes, also no. Yes, so you can use it to create three replicas and place them all on the same hard drive. No, in the sense that if a sector is slowly falling apart, there is noThere is no scientific way to find out and make a third absolute copy somewhere else. Echo promises procedures that can cause an entire CD to fail quickly, but you only notice it when an individual sector has decayed until you try. read directly, and by then it may already be a day Readiness An application cannot periodically run a test to read all three copies because it is not allowed to control which copy passes through it.)
- How can a short course of failure try to convince the voter and the voter that they are healthy (or sick)?
- start signal (simple, on the contrary, only detects power failures)
- internal controls (can be simple or complex)
- Pairing and comparison (high / low ratio)
- periodic analysis (for components that are not systematically trained)
- Timeout (end of timer means it is dead)
- Rent (no renewal means this tool does not work)
- Heartbeat (as long as he controls the ticking, he is alive)
- Keep-Alive (if he stops receiving calls, he will take advantage of this)
Several can be traced in this regard.
- page 14. Why do hard drive servers need to be more reliable than pass-through? (This seems to be an argument in favor of a dedicated server. If the server just needs to help you translate the disk log into disk software requirements – perhaps a one-to-one mapping – then it’s mostly small. If the server is handling file service requests for other potential buyers, it can become very popular, lose track of log activity on disk, or even fail, which can reduce the apparent reliability of a server – its disk website – on the same device as a huge file server. nameservers started right after a power outage, but a huge fileserver? You will probably need to do a restore / restore of all typical disk metadata before it can run on your filesystem, which will delay startup, the one withogo there is a nameserver m.)
- How would you coordinate investments in a dual port hard drive? What could be the problem? (The Echo document covers this on page 15. The tricky part is that two ports can be connected to different computers, and two computers try to use the hard drive at the same time.)
- Hard disk arbitration. This prevents the two requests from electrically communicating with each other, but a port 1 lookup captured by a port 2 lookup can also be potentially catastrophic. (Suppose the search is in a track and is recorded in the sector of the specified track.)
- Two-state lock (states: port A, port B) with hard disk hold, configurable from both CD controllers. Moves each controller farther away from the other, but requires a plan of action if the controller that detects the blockage fails.
- A two-state lock that cannot be completely cleared until the timer has expired a. Some trucks overcome the above problem. Cons: waiting timeI may be delayed if the primary failover controller fails. If the main controller is overloaded, the second controller goes to the second, in which case the second controller is overloaded, which is the problem that can arise.
- Tri-state blocking port (states: A, port B
Speed up your computer's performance now with this simple download.