It looks like some of our users are experiencing an event ID 2 password agent error. There are a number of factors that can cause this issue. Now we will deal with them.
Approved: Fortect
- 12 minutes to read.
Monitoring and reporting are important tasks after deploying Azure AD password protection. This article details the various monitoring methods, including where individual services log information and how to use Azure AD password protection.
Monitoring and reporting can be done either simply by using event log messages or by using PowerShell cmdlets. Both the DC agent and the proxy service write event log messages. All of the PowerShell cmdlets described below are only available in the proxy section (see AzureADPasswordProtection PowerShell Module). The DC agent software does not respect the PowerShell module installation.
Documenting The Circumstances Of The DC Agent
On each domain controller, DC Agent Expert Services records the results of each security check (and other status) and a local event log:
The DC Agent Administrator Log is the primary source of additional information on software behavior.I am.
Events rich in various Agent DC components fall into the following areas:
| component | Event ID Range |
|---|---|
| DC Agent Password Filter DLL | 10000-19999 |
| DC Agent Service Website Hosting Process | 20000-29999 |
| Logic for checking agent DC service policies | 30000-39999 |
Topic Administrator Event Log
Password Verification Result Events
On each individual domain controller, the agent DC service computer writes the results of each individual code check to a log of the DC administrator part of the agent.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

Typically, a successful password validation event is logged from the password filter DLL of the domain controller agent. Nearly every failed password validation operation typically logs two events, one from the DC Agent service and one from the DC Agent Password Filter DLL.
Discrete events to detect these situations are logged based on some of the followingfactors:
- Use or change the specific password for watching TV. Checkout
- Whether a valid password was entered successfully or not.
- If validation fails due to Microsoft global policy, company policy, or a combination of both.
- Whether the Audit Only policy is currently enabled or applies to the user’s current password policy.
| event | Change password | Password set |
|---|---|---|
| Skip | 10014 | 10015 |
| Error (due to client password policy) | 10016, 30002 | 10017, 30003 |
| Error (due to fallback to Microsoft password policy) | 10016, 30004 | 10017, 30005 |
| Error (due to combined Microsoft and customer privacy policy) | 10016, 30026 | 10017, 30027 |
| Error (due to username) | 10016, 30021 | 10017, 30022 |
| Audit only pass (will fail if client username and password policy failed) | 10024, 30008 | 10025, 30007 |
| Audit only pass (failed, Microsoft password policy took effect) | 10024, 30010 | 10025, 30009 |
| Audit only (would fail if Microsoft and client change policies were merged) | 10024, 30028 | 10025, 30029 |
| Audit-only-Pass (function does not work due to username) | 10016, 30024 | 10017, 30023 |
The spaces in the above table that refer to “combination policies” refer to situations where a user’s password can consist of at least one token from a specified list of Microsoft Denied Passwords and a Denied Password List for new customers.
The “username” cases discussed above are clearly related to situations where the username and password contain either the customer’s account name or the customer’s display name. Both of these scenarios cause the user’s password to be rejected after the policy is configured to enforce or is reached when the policy is in audit mode.
If the events of a pair are logged against each other, the two events are clearly related, requiring the same CorrelationId.
Summary Of Password Verificationah Reports The End Result In PowerShell
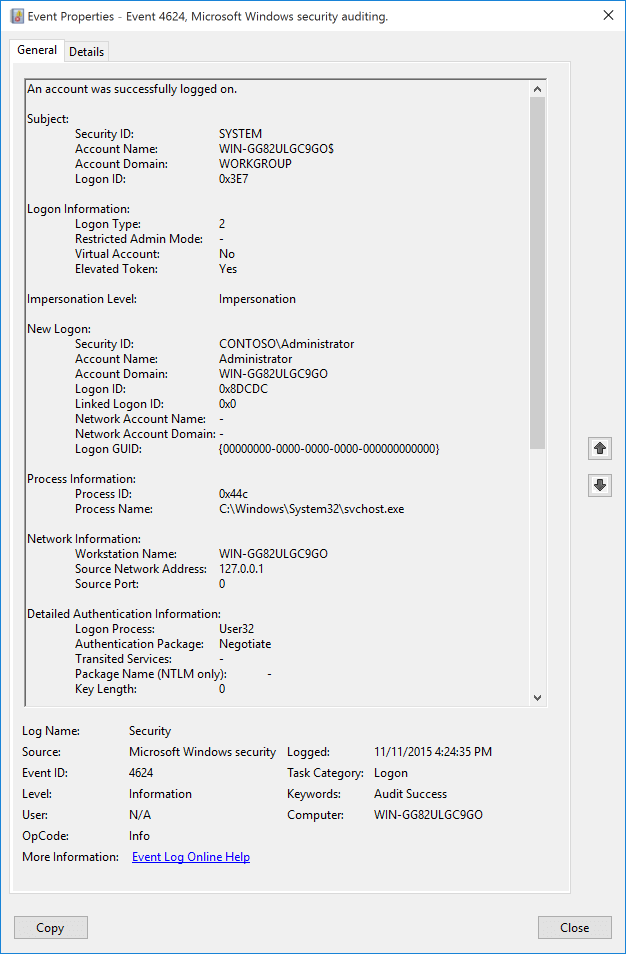
The Get-AzureADPasswordProtectionSummaryReport cmdlet can be used to get a summary of password verification steps. Sample output from this Fact cmdlet looks like this:
Get-AzureADPasswordProtectionSummaryReport -DomainController bplrootdc2Domain controller: bplrootdc2Password change confirmed: 6677Confirmed password: 9Password change denied: 10868Passphrase rejected: 34AuditOnly password change errors: 213PasswordSetAuditOnly rejections: 3PasswordChangeErrors. ... ... 0PasswordSetErrors: 1
The report scope for this cmdlet can be affected by any of the Forest, Domain, or Domain Controller recommendations. The absence of the a parameter means – Forest.
The Get-AzureADPasswordProtectionSummaryReport cmdlet queries the domain controller provider admin event log and then counts the total number of events that match each displayed result category. The following worksheet contains the intermediate assignments of each result and the corresponding event ID:
| Get-AzureADPasswordProtectionSummaryReport Property | Associated Performance ID |
|---|---|
| Password changes confirmed | 10014 |
| Password Confirmed | 10015 |
| Password change denied | 10016 |
| Passphrase rejected | 10017 |
| PasswordChangeAuditOnlyFailures | 10024 |
| PasswordSetAuditOnlyFailures | 10025 |
| Password change errors | 10012 |
| PasswordSetErrors | 10013 |
Note that the Get-AzureADPasswordProtectionSummaryReport cmdlet is provided to you as a PowerShell script and can be referenced directly in the following location if needed:
Sample Event Log Message For Event ID 10014 (password Change Successful)
The modified password required for the specified user has been verified against the current Azure password policy. Username: BPL_02885102771 Last name and first name:
Sample Event Log Message For Event IDs 10017 And 30003 (private Save Failed)
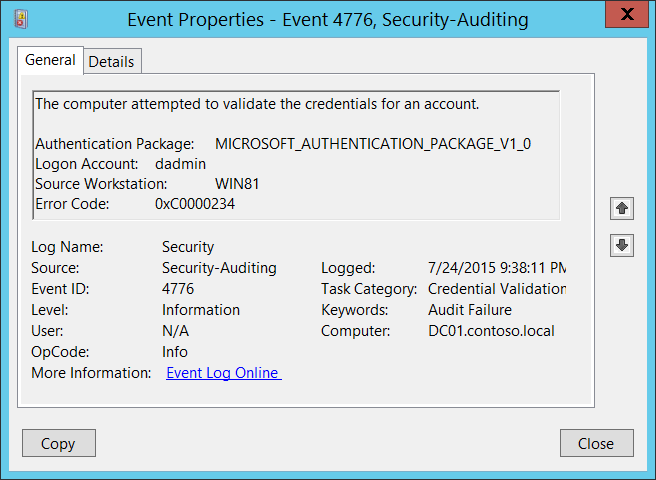
Resetting the password for the specified user was usually rejected afterHowever, it did not comply with the current Azure password policy. For more information, see the corresponding event log message. Username: BPL_03283841185 Last name and first name:
A password reset for the specified user only was rejected because at least one of the bride and groom matched the password set for each customer in the current Azure password policy. Username: BPL_03283841185 Last name and first name:
Sample Event Log Message For Event ID 30001 (password Was Accepted Because The Applicable Policy Was Simply Not Available)
Speed up your computer's performance now with this simple download.