In this guide, we will highlight some of the possible causes that can cause logon failure with Event ID in Windows Server 2008 r2, and then suggest possible solutions that you can use to try to resolve the issue.
Approved: Fortect
Windows Security Log Event ID 4625
4625: Account cannot connect
On this page
- Description of this event
- Field soil details
- Examples
- Discuss these possibilities.
- Mini-seminars for this event
This can be a useful event as it records and documents every failed login attempt to the local computer, regardless of login type, user location, or account design.
Randy’s Free Security Magazine Resources
- Free quick view of the security log
- QuantityWindows Event Section: Free Compressor Edition
- Free solution for auditing Active Directory changes
- Free Course: Secrets of Security Logs
Description Fields In 4625
Subject:
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

Identifies the provider that requested the connection, NOT the specific user who just tried to connect. The topic is usually zero or one of my maintenance principals and generally useless ideas. See “New Connection” for those who have just dived into the system.
- Security ID
- Account name
- Account domain
Username
Registration
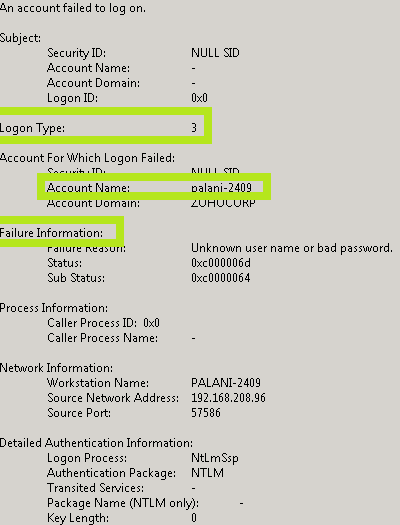
This is amazing information because it tells shoppers HOW the user just signed in: For a table of login type codes, see 4624 .
Account On Connection Failure:
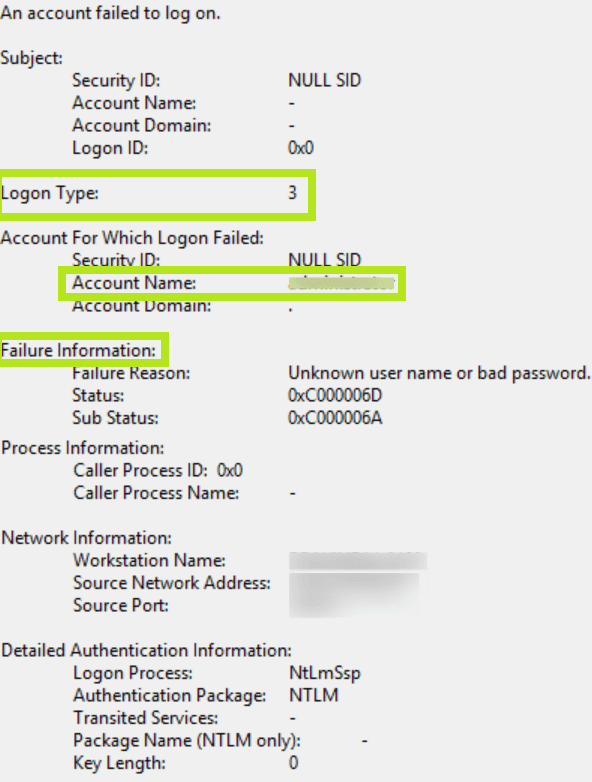
This indicates a user who tried to login and / or failed.
- SID: SID accountingthe first entry for which the connection was established. This is an empty field or NULL-SID if a valid account was not taken into account – for example, if the specified username absolutely does not match the valid login of the account.
- Account name: The account name specified when trying to connect.
- Account domain: domain or, if added to local accounts, computer name.
Error Information:
The message explains why the connection could not be established.
- Cause of error: Explanation of the text in case of connection failure.
- Status and Substatus: Hexadecimal codes explaining registration as the reason for the vehicle. Sometimes the substatus is filled in last, sometimes not. Below are the discounts we saw.
| Status also status subcodes | Description (not marked “error reason:”) |
| 0xC0000064 | Username does not exist |
| 0xC000006A | Full nameusername is correct, but the password is incorrect |
| 0xC0000234 | The user can be described as currently blocked |
| 0xC00000072 | Account is currently deactivated |
| 0xC000006F | A user tried to log in outside of the boy’s day of week or time of day restrictions |
| 0xC0000070 | Downsizing or violation of sandboxed authentication policy (matches event ID 4820 on a domain controller) |
| 0xC0000193 | Account Expiration |
| 0xC00000071 | Password expired |
| 0xC0000133 | Too high synchronization of clocks between DC and other electronic computers |
| 0xC0000224 | User must change password at next login |
| 0xC0000225 | obviously a bug in windows without risk |
| 0xc000015b | The user did not receive most of the requested logins (also known as logon privileges) through this computer |
Process Information:
- Calling Process ID: The process ID that was listed as logged in 4688 when the executable was run.
- Caller Process Name: Typically identifies the program executable that handled the connection. This is one of the trusted login elements named 4611 .
Network Information:
This section knows where the user was when registering. If the connection is started from the same computer, this information will of course be either blank or will reflect the respective local computers.
- Workplace name: the name of the computer, in particular the user, is physically present in all cases, unless this connection was initiated by a server application acting on behalf of the user. The workstation may also not bepopulated for some Kerberos connections, because in the case of user connections, the Kerberos protocol doesn’t really care if it’s tied to a computer account and therefore doesn’t have a marketplace to carry the workstation name in the request message options>
- Source network address: The IP address of the device on which the user is physically present in most cases, except when this connection was caused by a server application acting on the user’s behalf. If this connection can be initiated locally, sometimes the IP address must be 127.0.0.1 instead of the actual local private IP address. Sometimes this field is definitely blank because Microsoft says, “No, and the code path in Windows Server 2003 might be.” instrumented for the IP address, so it doesn’t always populate. “
- Source Port: Identifies the source TCP port connected to an account that has since seemed unnecessary to request as the source ports for most protocols were random.
Detailsabout Authentication:
- Registration procedure: (see 4611 )
- Authentication package: (see 4610 or 4622 )
- Successful Services: This is for servers where applications need to accept a different type of validation from the client and then pass Kerberos to the client components to access other resources. See http://msdn.microsoft.com/msdnmag/issues/03/04/SecurityBriefs/
- Package name: If this login was authenticated through the NTLM project (for example, instead of Kerberos), this field specifies which version of NTLM will be used. For security, see Network Security: LAN Manager Authentication Level
- Key length: The length of the key that protects the “secure channel”. See Security section “Domain Member Setting: Optimal Session Key Required (Windows 2000 or Higher)”. If the value is 0, the “Domain Member: Digitally Encrypt Street Protected Data (If Possible)” security setting will not work.