In this article, we will identify some of the possible causes that might lead to research into the impact of spyware, and then describe several ways to address this issue.
Approved: Fortect
Please Wait While We Check Your Browser
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

In my article, we discuss the different types of spyware and adware, their behavior and downloads.the threat of computers, and the spread of new types of spyware. Two in experiments that almost all study the frequency and effects of spyware found in popular P2P applications. Based on the results of empirical analysis, we are trying to raise the point of view of a more general view of spyware, based on the theory of (virtual) network of side effects. In the template, we classify what … label = “Expand Clipped Text”> Expand
Spyware Can Steal Commonplace Responses, Track Every Movement Of The User And Every Detail In Between. Learn About Most Types Of Spyware And How Best To Troubleshoot Infected Devices.
solve the problemGet help with specific situations with technology, your processes, and your projects.
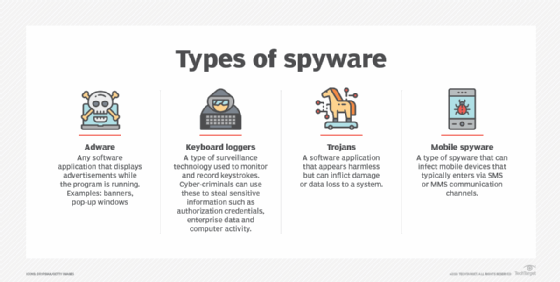
Spyware is considered a type of malware that confidently receives information from ignorant users. The effects of spyware range from collecting samples to usingmarketing purposes to simple targeted attacks by nation states on political activists. More advanced spyware will almost certainly be installed in the background, but spyware is often disguised as professional software or a browser extension – a Trojan horse – to hack into a device.

Spyware uses device websites to continuously track activity and record computer files, and then sends that data to exotic servers. The complexity of the spyware depends on the purpose:
- Adware and tracking cookies track the physical activity of the browser, including searches and downloads in history. This personal data may be used to place malicious advertisements or be sold to third parties. While this category refers to software, it can also refer to legitimate programs or browser extensions that collect information without the user’s consent.
- Keyloggers log keystrokes to collect sensitive information as well as global yesdata. They can be used by a company to track employee activities, law enforcement investigating criminal activities, or celebrities to steal credit information, card numbers, and possibly other personally identifiable information.
- Information theft is a type of malware that extracts more targeted data. For example, hardware thieves keep track of which apps or web pages you use and directly retrieve personal information or credentials, rather than collecting that information as you type. Thieves of information can also steal actual documents and media.
- Banking Trojans such as Kronos and Emotet are even more targeted spyware used to attack banking companies and steal confidential information processed by other systems.
- System Monitors are various advanced forms of spyware that can be used by law enforcement agencies. This software tracks your browsing habits, useapplication usage and keystrokes, like other forms of spyware, unfortunately, can capture audio and video from the microphone and camera of the device too efficiently than GPS location data. The most sophisticated system monitoring spyware like NSO Group’s Pegasus can even record chats from end-to-end encrypted messaging systems like iMessage or WhatsApp-Signal.
Affects Your Device
While it has always been known that spyware slows down computers, the slowdown effect is becoming more complex in terms of perception, as computers and mobile devices become more powerful.
Other signs of a spyware infection on your device:
- It often runs abnormally slowly or during certain activities.
- The home page of the web browser has been changed or new web browser extensions have been installed without any further action.
- Anti-spyware / malware programs are not working as expected.
- devicehas established wired connections to known malicious servers.
- The camera or microphone in the method is activated without user action.
It’s important to note that adware doesn’t have to be functional. Malware errors can be an excuse for system or program crashes – another sign of spyware.
How To Remove Spyware
Fortunately, some modern security tools can detect anomalous links and spyware. If a particular computer has been infected, installing anti-spyware, powerful software, or antivirus software from vendors such as Citrix, Bitdefender, Kaspersky, Sophos, Trend Micro can detect and remove spyware known to Malwarebytes and protect against other potentially redundant software. … Note that more advanced spyware may try to disable security tools to avoid diagnostics. Therefore, it is advised to save money from time to time to ensure that the security tools are working as expected.
Removing spyware from a mobile device can be more difficult depending on the depth of the system integration. Often the only option is to perform a full factory reset and reinstall the roaming operating system from a clean system image.
This was the last post in May 2020.

