Here are some simple steps that can help you solve WiFi password cracking problem in Windows XP.
Approved: Fortect
Can Portable Penetrator run on Windows XP?
Can we hack unknown WiFi password?
Many women ask how to hack Wi-Fi passwords using Android, and they may or may not. The simple answer is yes. ” Users can hack Wi-Fi passwords on Android devices with a few tips and methods (apps).
Yes, you can easily recover WPS PIN passwords with VMware Player and WPA WPA2.
See Portable Penetrator WiFi Finder Software here:
How can I get my WiFi password from Windows XP?
In the Network Connections window, press and hold the message, or right-click the network name and then click Status. Click Wireless Properties. Select the Security checkbox and select Show Symbols. The wireless network code can be found under Network Security Keys.
Hacking the awesome Windows Wi-Fi password seems like a great idea, but if you have access to a computer connected to your current network, you might have to avoid other methods.
Which software is best for hack WiFi password?
Protect your Wi-Fi network from attacks with Wi-Fi password cracking prompts. Easy-to-use WPA WiFi account information cracking software for installation on Windows 10 or Mac OSX platform. Find out how attackers are uncovering Wi-Fi secrets and methods and securing your Wi-Fi network before it’s too late.
Windows XP was an incredibly powerful operating system when it was first introduced to the general public, but over time Microsoft introduced powerful new operating systems and support for Windows XP ended.
However, this does not mean that not many people still use this standard operating system.
If you or someone close to you are using Windows XP, getting your company password is a fairly simple way. Here’s how it works:
Access To Your Computer
Let’s say your neighbor is using Windows XP and you need access to that Wi-Fi network. Best of all
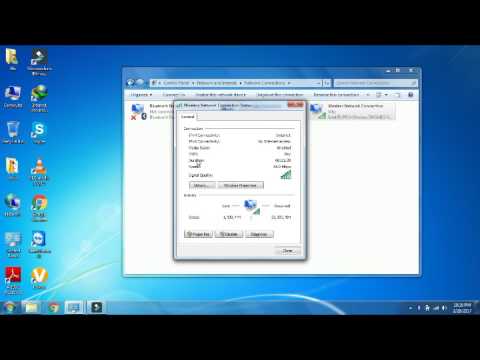
To enjoy this, just check your computer.
Well, how do you do it? Well, maybe you canWould you like to go to him and ask him to set up his computer for a while? This gives you short term access.
Then, when you are online, you just need to click on the bar in the lower right corner that indicates to you that this network signal is displayed, then select the connected network with the right mouse button and finally Properties disappear.

From there go to the Security section and you will be able to determine your password and SSID (this is the name of the network).
Right below it, you will probably see a small field that you can definitely check the box, namely “Show password”.
Click most often and the fields to see your password right in the filter.
If you check the box again, the password is hidden again, and you can safely walk away and tell them that your effectiveness has been achieved. Then just successfully connect it to the network, but this time enter the password you found earlier.
And as you can see, you’ve successfully reconnected to the network!
Use A Brute Force Destroyer
The next option is to use an awesome attack tool.
Usually one hundredThe standard wireless encryption provided by Windows XP is WPA, and the most recent is WPA2.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

However, if you have an updated wireless card and driver, you should also use WPA2-PSK encryption.
No matter what kind of encryption you use, using any brute force tool to gain access to the real web is considered illegal the moment you get permission from their MLM without their permission.
Download a powerful gadget like the Reaper Crack and get started with your idea. The program will try to match each character in the password with Cash Drawer 1 in the database until it can effectively understand the global password.
Depending on the complexity and length of the password, this may take some time.
However, if buyers have time and time, you can leave the tool running in the background.


