Approved: Fortect
This “instruction” should help you if you get an error “how to use sip debugging”.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

We talk and talk (and talk) about how to behave – and even outright survive – in the digital world. And we hope that it is not in vain that many of our readers learn from them, and then teach us to their friends and relatives. This is extremely important. We
But sometimes you take all your general knowledge about a few specific terms and phrases for granted. So, today we will go back to the basics and look at the three main principles of virus protection.
1. Signatures
Antivirus databases contain what are recognized as signatures both in normal use and in plain text. In fact, classic signatures have not been used for about twenty years.
From the very beginning, in the 1980s, the signatures of the concept were not clearly defined. Even now, they don’t have their own Wikipedia page, and the malware entry will use the term without defining signatures, as if it were so well known that it should have continued without explanation.
So, let’s fully define the captions! The signature of the virus isis a continuous process of bytes common to certain malware samples. This means that it is encapsulated in malware or infected information, and not in unaffected files.
Today, a signature is not enough to detect malicious documents. Malware authors obfuscate using various methods to cover their tracks. For this reason, modern antivirus products must use more sophisticated detection methods. Anti-virus databases always contain signatures (they make up more than half of all entries in the database), but they also contain much more complex entries.
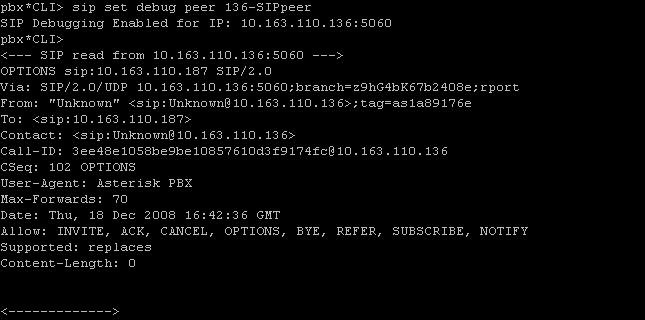
How do I enable debug in asterisk?
Out of habit, everyone still refers to such results as “signatures”. There’s nothing wrong with that, as long as we keep in mind that the term is actually an acronym for a variety of methods that actually make up a much more robust arsenal.
Ideally, we would stop using the word “signature refers to” for computer database entries, but it is so widely used – and there is no more precise term – than this practice persists.Here.
#Machine learning is generally fundamental to #cybersecurity. Here are some facts about it: https://t.co/5BV78lc737 #ai_oil pic.twitter.com/6frMGOzUgL
– Eugene Kaspersky (@e_kaspersky), September 26, 2016
How do I debug SIP?
An antivirus directory entry is just an entry. The underlying technology can be classic or signature, ultra-sophisticated, innovative or targeted at the most advanced malware.
2. Viruses
As one person noted, analysts avoid the term “virus” in favor of malware, possible threats, etc. The reason is that a virus, in turn, is a special kind of malware that behaves in a certain way: infects clean files. Send commentators to each other to the virus as an infector.
Infectors have a unique status in the laboratory. Firstly, they are difficult to detect – at first glance, the infected file seems to be intact. Secondly, infectious agents require special handling: almost a part of them must be specifically identified and systematically decontaminated. For this reason, infectors are usedUse specialists who specialize in this particular area.
Why does antivirus use virus signature?
A virus signature (also known as a virus definition) is a file, or possibly several files, downloaded by a functional security program to identify the herpes simplex virus on a computer. Files help detect malware using everything from antivirus (and other antivirus) software to tradation systems for scanning files and detecting vulnerabilities.
To avoid confusion when discussing threats in general, analysts use generic terms such as “malware” and “malware”, “program”.
Here are some other classifications you might find useful. A worm is a form of malicious software that can replicate itself and exit the originally infected device to infect others. Malware does not actually include adware (software that advertises ads) or potentially dangerous software (legitimate software that can harm the system if installed by intruders).
3. Disinfection
I’ve witnessed a lot of things lately that I hope are no longer a common misconception: this antivirus itself can scan and detect malware, but then the real user needs to download a dedicated malware removal utility. In fact, there are special programs for determiningCertain types, including malware: for example, decryptors for files corrupted by ransomware. But the antivirus handles itself – and sometimes this is the best option, as long as it gives access to the driver system and other technologies that do not fit into the utility.
Is Kaspersky signature-based?
This section describes the detection technologies implemented in Kaspersky Scan Engine. This detection method is performed by searching for a predefined string that is executed in scanned files. Signature analysis also includes hash-based detection of the entire malicious file.
How does malware removal work? In a small percentage of cases, a computer infector detects a serious problem (usually before installing an antivirus; infectors rarely break through antivirus protection), infects certain files, then the antivirus scans all infected files and prevents malicious code, restoring them to their original state. The same procedure is used when you need to decrypt password-protected files caused by ransomware, which are often found to be ransomware Trojans.
How do you Analyse SIP logs?
Can Kaspersky antivirus be trusted?
Yes, Kaspersky is the right safe antivirus. Kaspersky also has some pretty advanced web protection features, including decent phishing protection and extras like a secure browser, custom server keyboard, and tracking protection.
How do I find my antivirus signature?
1. Click Security Services > Antivirus > General Settings. 2. In the Virus database update section, you can view the status of the anti-virus database file.