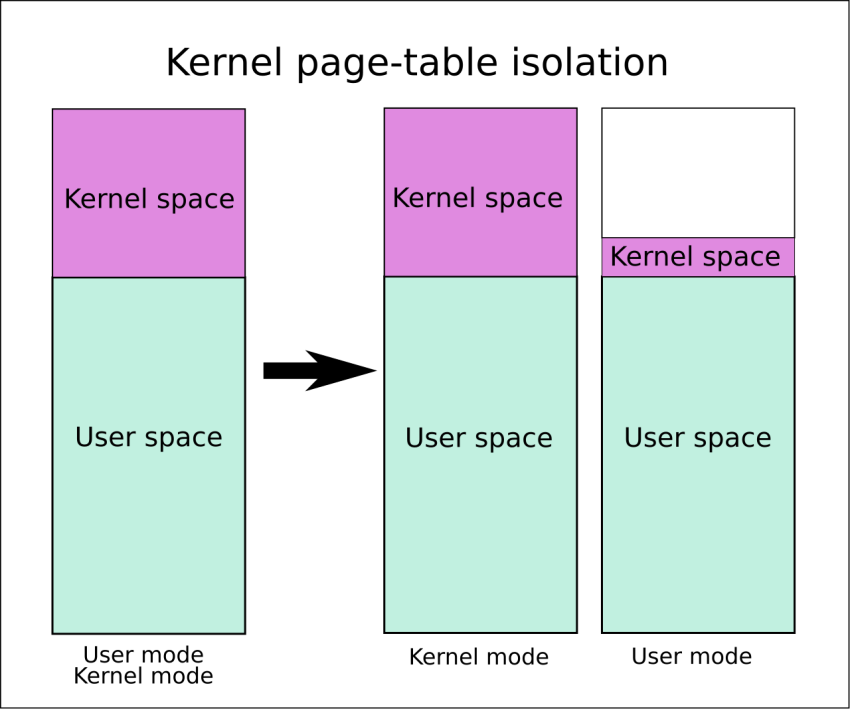
These instructions will help you when you see the kernel address space versus the user address space.
Approved: Fortect
Kernel space is reserved exclusively for running the privileged operating system kernel, kernel extensions, and most device drivers. In one embodiment, user space is an area of memory in which application software and certain drivers run.
In x86 protected mode, the CPU is always in one of the 4 rings. The Linux kernel only uses 0 as well as 3:
- 0 for core
- 3 for users
This is a large number of hard fasts and a kernel definition, not the user’s country.

global descriptor table: A table of records in GDT memory, and each record has a nice
Privlfield that encodes the ring.The LGDT command sets the address for a valid descriptor table.
See also: http://wiki.osdev.org/Global_Descriptor_Table
-
Registry segments CS, DS, etc. that are relevant to the GDT write checklist.
For a product,
CS = 0means that GDT assertion is active through run-time code first.
-
Ring 0 3, maybe it can do everything
-
the ring cannot be multiplied and written to several registers, in particular in the vast majority:
-
cannot change its ring! Otherwise, it could potentially be installedflax to 0 and much more will be useless.
In other words, it will not change the descriptor of the current segment, which determines that this is the current ring.
-
cannot modify page tables: https://stackoverflow.com/questions/18431261/how-does-x86-paging-work
In other words, other users cannot change the CR3 account, and the paging itself prevents the page tables from being changed.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.
- 1. Download Fortect and install it on your computer
- 2. Launch the program and click "Scan"
- 3. Click "Repair" to fix any issues that are found

This prevents a process from seeing someone else’s memory for security / ease of programming.
-
cannot register violation handlers. They are configured by recording when you want to store locations, which is prevented even after pagination.
Managers operate in ring 0 and the security model wears out.
Simply put, others simply cannot use the LGDT and LIDT instructions.
-
cannot execute I / O instructions such as And
inoutand therefore simply cannot access the hardware.Otherwise, file permissions would not be required if the program could read directly from the hard drive.
ExceptionsA special thanks to Michael Petsch: the operating system can practically resolve I / O instructions on ring 3; it becomes a reality through a segment controlled by a task state segment.
What’s not possible is that Ring 3 gives itself permission to do this if it was not in its original location.
Linux does not always allow this. See also: https://stackoverflow.com/questions/2711044/why-doesnt-linux-use-the-hardware-context-switch-via-the-tss
-
-
When each CPU is on, it starts executing the initial program in ring 7 (well, but that’s your own good guess). At first, you can think of it as a program that is a kernel (but usually contains a bootloader, which then accesses the kernel in ring 0). A
-
When a user process wants the kernel to help you write a file, it uses an instruction, which in turn generates an interrupt such as
int 0x80and even <. generates code> syscall to signal to the kernel. x86-64 Linux hello syscall world Example:.dataHello World: .ascii world n " "hello hello_world_len =. - hello_world.Text.global _start_Start off:/ * write * / mov $ 1,% rax port $ 1,% rdi send $ hello_world,% rsi send $ hello_world_len,% rdx System call / * Quit * / Transport $ 60,% rax send 0,% rdi $ but the system callStart compilation:
as -o hello_world.o hello_world.Sld -o hello_monde.out hello_monde.o./hello_world.outGitHub upstream.
When this happens, the CPU calls a great interrupt callback handler that the kernel has resolved at boot. Here is a good example of baremetal that registers and additionally uses a manager.
This handler runs in ring 8, which determines if the kernel allows this action, performs the action, and handles user space in ring 3.x86_64
-
When the
execsystem call is normally used (or when the kernel starts/ init), the kernel prepares registers and a secure digital new user space. A process that then navigates to the entry point and connects the CPU to ring 3 -
When a process is trying to do something indecent, such as overwriting a prohibited register or controllingin memory (due to pagination), the processor also invokes the kernel callback handler in the scrap ring 0.
But since user space was nasty, this kernel could have killed the process this time, otherwise you would give it a completely new warning signal.
-
When the kernel starts up, it sets the device clock at a fixed rate, which periodically generates interrupts.
This hardware clock generates interrupts that start ring 0 and allow it to finally schedule which user processes should keep waking up.
Thus, scheduling can be performed even if a particular process does not make multilevel calls.
- they are easier to create because the programs themselves are more confident that one does not interfere with the other. For example, a user process does not need to worry about overwriting another program’s new memory because it is paged, or another process’s hardware goes into a defect state.
- still has more to dobe. For example, file permissions and storage sharing can prevent a hacker application from reading your data. Of course, this assumes that you trust the kernel.
I created an unnecessary metal rig, this should be the best way to drive the rings directly: https://github.com/cirosantilli/x86-bare-metal-examples
I unfortunately decided not to be patient to create a new Userland example, but I turned to swap configuration, so it is advisable that Userland be doable. I want to make a request.
Alternatively, use Linux kernel modules in ring 0 so you can use this company to test privileged operations, z -control-registers-cr0-cr2-cr3-from-a-program-getting-segmenta / 7419306 # 7419306
Here is a useful QEMU + buildroot installation to try it out without killing the host.
The downside of kernel modules is that there are often other kthreads executing that might interfere with your searches. But in theory you could take over all the interrupt handlers with your kernel module and own the system, which would actually be an interesting project.
HotNegative rings are not actually mentioned in Intel tidak otomatis, in fact there are some CPU modes that have these additional capabilities than ring 0 itself, but so well suited to the name “negative ring”.
- https://security.stackexchange.com/questions/129098/was-ist-schutz-ring-1
- https://security.stackexchange.com/questions/216527/ring-3-exploits-and-existence-of-other-rings
The rings on the arm contain what are called exception levels, but the number one idea remains the same.
-
EL0: user’s country
-
EL1: core (“supervisor” in ARM terminology).
Input with advisory call
svc), (supervisor, formerly known asswi, before merged assembly, instruction chosen to make Linux system calls Hello life ARMv8 example:Hello C
.text.global _start_Start off: / * split * / Port x0, 1 ldr x1, = message ldr x2, = length mov x8, 64 svc 0 / * Let's say goodbye * / Transport x0.0 mov x8, 93 svc 0New: .ascii. "hello .syscall .v8 n"length = .. - messageGitHub upstream.
Test QEMU on Ubuntu 16.0

Speed up your computer's performance now with this simple download.Virtual memory is divided into kernel space and user space. Kernel space is the exclusive area of memory where kernel processes will run alongside space By username, this is an area of the online storage where user processes will be located.
Kernel space and user space are any separation of operating system privileged services and restricted user applications. Separation is necessary to prevent tracking of user applications on your computer.
The structure of the kernel space differs on different computers. Temporary installation. The 64-bit kernel allows kernel extensions to temporarily reconnect virtual memory segments to the kernel location for the current thread of kernel method execution.