Approved: Fortect
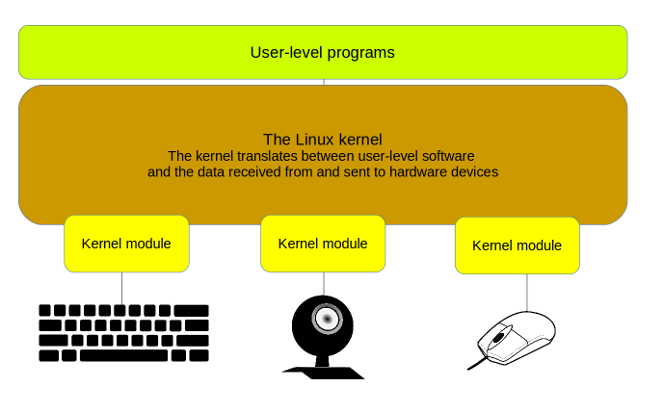
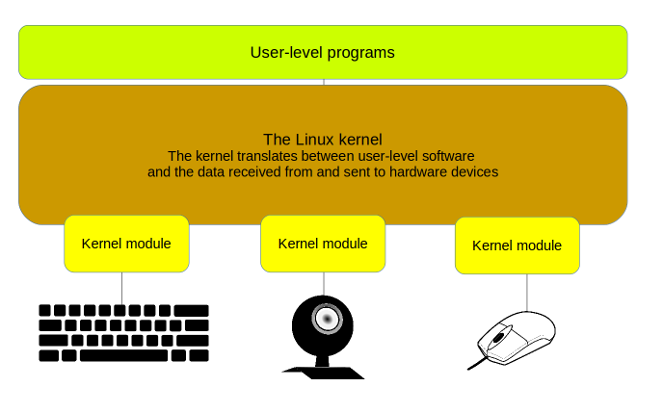
Sometimes your computer may display a message pointing to the ISSC Linux kernel module. This error can be caused by a variety of reasons. The Linux kernel is the main component of a GNU / Linux compatible system. Linux kernel functionality can be extended without restarting the system using kernel modules. A kernel module is a voucher code that can be loaded and unloaded into the kernel as needed.
Dust Some New (old) Vulnerabilities
Have you ever accidentally looked at the code forLinux vendor?Core and thought, “Wait, this can’t be true”?We assessed this position in ourselves when we discovered three discrepancies inforgotten corner, I would say that the main Linux kernel that turns out to beabout 15 years. Unlike most problems in which dust accumulates,These pests have always proven to be beneficial, so they have proven that they can be used. Incidentally, local privilege escalation (LPE) in various Linux environments.
Who Are You Calling At SCSI?
Subsystem in question – (Small computer scsiSystem Interface) data transmission, which is the current transmission standardData for meeting computers with devices, initiallythrough any physical cable such as hard drives. SCSI is a respected standardwas originally released around 1986 and was the first choice for home servers as welliSCSI is primarily SCSI over TCP. SCSI is still in use today, especially The actual event you are dealing with is related to some storage activity, but how does this work?to be a required interface on a standard Linux system?
Magic ExpandedThese package dependencies turns rdma-core into packages received when installing one of the RHEL orBasic CentOS environments with great GUI (workstation, server withGUI and virtualization host) and Fedora workstations.Also rdma-core can be installed on other pins, Ubuntuincluding Debian as this item is used as a dependency for someother packaging (see figure 1). This was enabled by default in Ubuntu Server 18.04 and earlier.
RDMA (Remote Direct Memory Access) is a technologybroadband, for low latency advertising, applied to dataTransmission and computer memory seem obvious. There are several implementationsbut for some reason the only one that is relevant to the current discussionInfiniband found in my ib_iser kernel module. You
if you think “wait, things could be up automatically”works even if i’m not using SCSI or iSCSI? “It’s great becauseIf you ask a question, you will find out what the concept of a kernel can do on demand vania. Module refactoring and an attack vector that has been around for a long time.
Automatic module loading, also known as “crufty-kernel-code” on demand
To be helpful and to improve compatibility, all LinuxThe kernel can load kernel programs on demand when certain code detects something. Functionality should be mandatory and it should be possible to charge, for exampleFamily protocols. That’s all, but it also opens the holdA surface for local attackers as it allows unprivileged users to download dark core units that can then be mined. Public awareness of it has been around for over ten years and grsecurityGRKERNSEC_MODHARDEN is associated as an entered protection against this kind.Dean in 2009. John Oberheid’s ironic problem, named a public exploit in 2010, turned it into a problem, Dan Rosenberg’s proposal for a patch in 2010 The full sysctl option has not been implemented. There were really othersHowever, the mitigation measures that have become availableAre available in recent years,Their support varies depending on the Linux distribution.
So Are You Telling Me There Are Mistakes?
One of the most important aspects of source code ownership is that the public can easilyscan visually and various objects can jump and annoy your loverInteresting, so you want how the thread is pulled over them. The first mistake most of us makefound like this. Seeing a simple sprintf just means no copy bufferLength, which means where is the data controlled by the attacker andlack of preliminary size check (see figure 2). So, the truth is that there are quite a few redirects and hence macros, and you have Jump by number of files to track the execution location,The main thing is a simple correct buffer overflow because sprintf was usedalso indicates a corresponding lack of safety-oriented programming.Practices that may prevail at the time of the development of this Code, such as display other errors ki.
The error is similar in several respects: using the kernel address as the master.Obviously a holdover from the days when there was no effort to keep the coredripping pointers, but these days it’s a simple kernel address spaceRandom Layout (KASLR) is circulating because it points to a structure that fully matches Needle. And the last mistake is simply not validating the data withuserland, classic kernel and also a multimedia problem.
Linux Kernel Buffer Overflow
How to sign and load a kernel module?
To sign and link kernel modules, you must: 1 Install the appropriate utilities in your program. 2 Authenticate the kernel part. 3 Create a pair of public and private responses. 4 Import the public secret into the target system. 5 Sign the kernel module with a private critic. 6 Load the signed kernel element.
-
Vulnerability Type: Heap Buffer Overflow
-
Location: iscsi_host_get_param () in
drivers / scsi / libiscsi.c< / p> -
Affected Tested Versions: Via RHEL 8.1, 8.2 and 8.3
-
Effects: LPE, Information Leakage, Denial of Service (DoS )
-
CVE number: CVE-2021-27365
How to display kernel module information with modinfo?
Display information about a Linux kernel module using the Modinfo command. 1 1. Displaying the author of a kernel module (manufacturer) To display the author of a kernel module, use the author flag. 2 2. Display the description of the kernel module. Step 3 3. Review the license for the kernel module. 4 drugs. Show kernel module parameters. 5 5. Viewing the dependencies of kernel modules.
The first vulnerability is full buffer memory inISCSI subsystem. The vulnerability can be described as being caused by the creation of an iSCSI franchise.Set the World Wide Web to a value greater than a and then try reading it .Internally some sort of sprintf call (line 3397 appears in drivers / scsi / libiscsi.c in kernel source 4.18.0-240.el8) will probably be provided by the userThe one page barrier used is actually for the seq file which issupports all iscsi attributes. In particular, a disadvantaged person canSend netlinks to each iSCSI subsystem (in drivers / scsi / scsi_transport_iscsi.c ), sets of attributes assigned to the iSCSI connection like hostname, username, etc. via in < code. Send the helper functions that appear> drivers / scsi / libiscsi.c . These attributes are only determined by the size of the maximum length of yourNetlink message (2 ** 32 or 2 ** 16 depending on the code usedProcessing I would say the message). Sysfs and seqfs subsystems can be used respectivelyto read these attributes, but keep in mind that it only uses the bufferPAGE_SIZE (single_open in fs / seq_file.c , called when a sysfs file of a particular type is opened). It looks like this bug first appeared in 2006 (see drivers / scsi / libiscsi.c , commits a54a52caad and fd7255f51a) whenISCSI was supposed to bedeveloped. However, the kstrdup / sprintf form used in the bug has changed. Expanded since the first commit to cover more specialties. Core
Linux Pointer To User Space Leak
-
Vulnerability type: Kernel pointer leak
-
Location: show_transport_handle () in driver / scsi / scsi_transport_iscsi.c
-
Affected Versions: RHEL tested on 8.1, 8.2 and 8.3
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.
- 1. Download Fortect and install it on your computer
- 2. Launch the program and click "Scan"
- 3. Click "Repair" to fix any issues that are found

Impact: Information Leak
-
CVE number: CVE-2021-27363
In addition to the heap overflow vulnerability, GRIMM discoveredA kernel pointer leak that could potentially be used to determine a structure-related address.iscsi_transport. If the iSCSI card is registered withthe iSCSI subsystem, the “handle” of its transport, is accessible to humans.unprivileged via sysfs filesystem, via / sys / class