Approved: Fortect
Hope this guide helps you learn how to remove Vista 2010 malware.
Step 1. Disconnect from the Internet normally.Step 2: enter safe mode.Step 3. Check your Activity Monitor for vengeful apps.Step 4. Run the malware scanner.Step 5: Repair your web browser.Step 6. Clear the cache.
Security Tool XP 2010, XP Defender Pro, VistaSecurityTool 2010 and Vista Defender Pro – the new bad guysexactly what the same program is for. They are confirmed only by different names and interfaces.Depending on which Windows application it is running in. This guide is underseveral different names I have listed will make your diet healthier depending on the versionfrom Windows:
|
fraudulent Windows XP name |
Fraudulent Windows Vista name |
Rogue Windows 7 name |
| AntiSpyware XP | AntiSpyware Vista | AntiSpyware Win 7 |
| AntiSpyware XP 2010 | AntiSpyware Vista 2010 | AntiSpyware Win 4 2010 |
| XP Antivirus | Vista Antivirus | Antivirus Win 7 |
| XP Antivirus 2010 | Vista Antivirus 2010 | Antivirus Win 7 2010 |
| Complete XP Security | Complete Vista Security | Complete Win 7 Security |
| XP AntiSpyware 2010 | Vista Guard | Win 7 Antispyware 2010 |
| XP Antivirus Pro | Vista Tool | Security 7 Antivirus Pro |
| Guard XP | Vista 2010 Security Tool | Get 7 guards |
| XP Security Tool | Vista Smart Security | Tool without Dangers of Win 7 |
| XP Security Tool 2010 | Vista Smart Security 2010 | Win 7 2010 Security Tool |
| XP Smart Security | Vista AntiMalware | Win 7 Smart Security |
| Intelligent Security XP 2010 | Vista AntiMalware 2010 | Win 7 Smart Security 2010 |
| XP Malware Protection | Vista AntiSpyware | Win 7 AntiMalware |
| XP AntiMalware 2010 | Vista AntiSpyware 2010 | Win 7 AntiMalware 2010 |
| XP Antivirus Pro | Vista Antivirus Pro | Antivirus Win 7 Pro |
| Experience Defender | Vista Defender | Winner of Six Defenders |
| XP Defender Pro | Vista Defender Pro | Defender Win 7 Pro |
| XP Security | Vista Security | Win 7 Security |
| Security XP 2010 | Vista Security 2010 | Win 7 Security 2010 |
| Internet Security XP | Vista Internet Security | Win 7 Internet Security |
| XP Internet Security 2010 | Vista Internet Security 2010 | Win 7 Internet Security 2010 |
How do I manually remove malware?
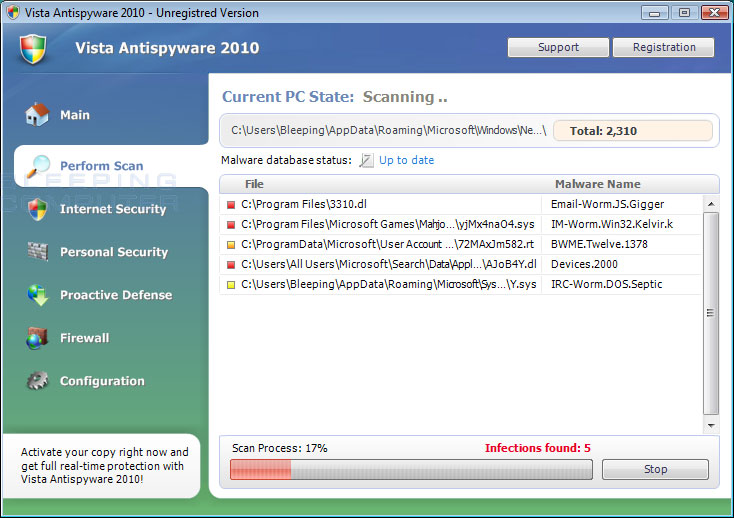
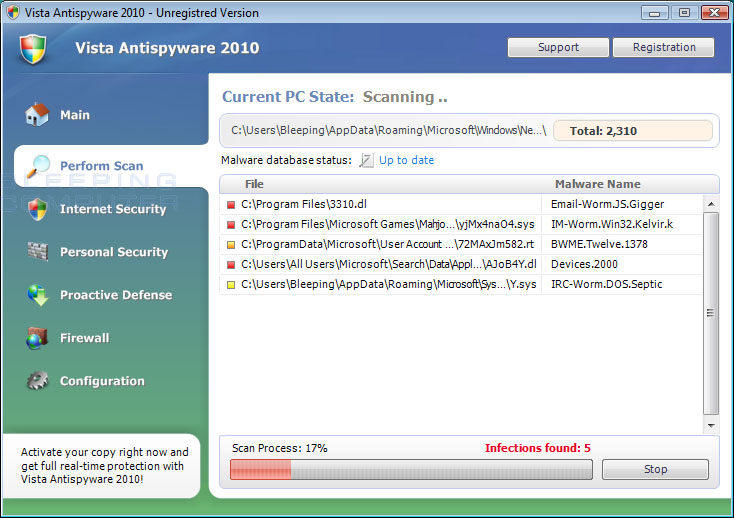
When this rogue is installed, it sometimes pretends to be a Windows update that is already in progress. establishedAutomatic updates. It is then named this single executable file. installedAV.exe, which runsIt implements very ambitious methods to ensure that the public cannot remove it.this is. First, it makes sure that when the executable is launched, it will run instead.XP 2010, XP Pro Defender or Vista Pro Defender Security Tool. What if it turns out to be originalThe program you were trying to run thinks the villain is safe, so it probably will.let’s start too. In this way, a specific villain can determine which executables you want to have.run to you, come back, protect you. it will change for sureButtons to when starting FireFox or possibly Internet ExplorerSnape in his place. and display a fake firewall warning. Last but not least, ifAttempting to navigate to the website for you will hijack your business browser and state thatThe website is a completely new security system and the risks prevent you from helping yourself while you are visiting. Started
Once the villain really enjoys all the other villains, he will scan your main computer.and they report that they have had a lot of infections. If you tryThe program for the removalone of these infections, the choice of which indicates that you needfirst purchase the program. In fact, however, the infection that attackersThe conditions on your primary computer are all valid files that, if deleted, could causeWindows does not work as expected. So please don’t believe thingsConditions are infections.
When starting XP Security Tool 2010, XP Pro Defender, Vista Security Tool2010 and Vista Pro Defender will also display fake updated security warnings onA computer. The text of some of these security measures:
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.Approved: Fortect

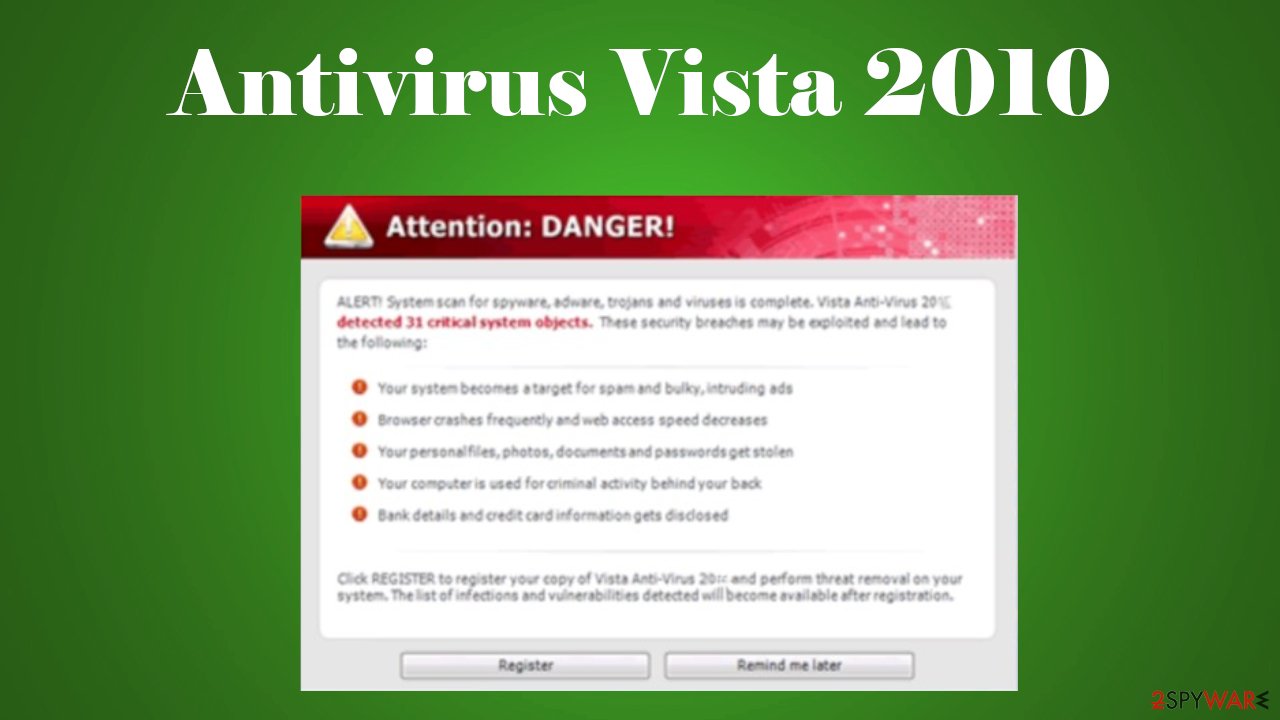
Tracking software found!
Your PC activity is getting ready to be monitored. Potential spyware infection. Your datasecurity can potentially be compromised. Confidential data can be stolen. Prevent damagenow, having completed the security analysis.
To remove malicious websites from your system, follow these basic considerations: download the perfect malware removal tool like McAfee Stinger (or another tool like basic antivirus) to a separate computer, and save it to a USB drive. Depending on the malware in question, you may need to use other similar systems.
XP Internet Security 2010 Firewall Warning!
XP Internet Security 2010 blocked the program from the siteInternet
Internet Explorer infected with Trojan-BNK.Win32-Keylogger.gen
Private facts can be stolenare given by third parties using credit card details.and passwords. I like
just get the results, these false warnings and security messages are allfalse and should be ignored.
Without a doubt, this thief was created to steal your money while kidnapping you.your computer and try to make you believe that you are infected. Because of this,Please stop buying this program and, if your organization has one, check your balanceThe card company also pays legal fees. Finally, to uninstall XP Security Tool 2010,XP Defender Pro, Vista Security Tool 2010 and Vista Defender Pro impress with usethe instructions below contain only free software. Security
Options To Uninstall XP Tool 2010, XP Defender Pro, Vista Security Tool 2010 And Vista Defender Pro
Self Help
This tutorial has detailed instructions, but it’s written in a way that everyone can follow. Make sure your data is backed up before proceeding.
If you are uncomfortable making changesinto your computer or take any of these actions, don’t worry! Instead, you will most likely get a free one-on-one interview by asking questions on the forums.
- For the first part of this removal guide, you will need to do another exercise.Computer than infected. This is also difficult to remove, soPlease follow the instructions carefully. If a customer is wondering ifor not, you should be able to do it, do it, not like I just simplified these instructionsfollow the opinion of people with computer knowledge.
- Download Malwarebytes Anti-Malware or MBAM from another technology.and all the reg files in the following locations and therefore save them in an externalThe media loves it simply because it has an external hard drive or USB stick. Then we usean external flash drive or drive to share these files with yourA computer. If not everyone has a USB drive, you can purchase one from any other local vendor for a price.or an online computer store for a slight edge. Examples of good and cheapyou can easily find them on Neweggand
Open Windows Security Settings.Select Virus & threat protection> Scan options.Select Windows Defender Offline Scan, and then select Scan Now.
Malwarebytes Anti-Malware download link(When loading, the home page opens in a new window) – Everyone should download this
FixExe.reg- Everyone should
Is there a truly free malware removal tool?
How do I remove suspicious malware?