If you see users in Windows NT error codes on your computer, you should take a look at these fix methods.
Approved: Fortect
Windows NT is the operating system that manages sessions. Therefore, when starting the system, you will probably need to log in with the name е and password. When Windows NT is installed, an administrator account is created for payment, as well as an account named “Guest.” It is possible (recommended) (and end user permissions to change (the actions they are allowed to do) and create users using the User Manager. 
User Management
User Manager is a standard Windows NT utility that experts say manages subscribers as the name suggests. It is available in the start menu (Programs / Administration Tools).
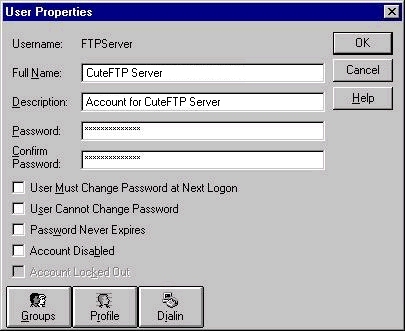
Typically, to create an appropriate new account, click New User in the User menu. Opens a dialog box for entering information about this specific new user:
- User: login of the current user.
- Full name: additional information about the user.
- Description: Optional field.
- Fields for d Password: optional, but it is recommended that you fill in this company and activate the field that says “User must change thumb password for security purposes”.
User Naming Conventions
User naming events are how the administrator decides to discover users. The following should be noted:
- Usernames must be unique (on the website or on the local computer).
- User accounts can contain upper or lower case letters, this should be used in the following cases: / [] -. | =, + (empty)? <>
- Avoid creating similar usernames.
User Accounts And Security
There are two types of profiles in NT. Built-in accounts are accounts created by your business. After installation, Windows NT is configured with built-in accounts (pending accounts and guest administrator). First of all, it provides minimal security.
- Accounts you create: user accounts withknitted with network connectivity and access to system resources on the network. These accounts contain general information about the user, including their name next to this password.
- Guest: This allows regular users to log in, and I would suggest accessing the local machine. It is indeed disabled by default.
- Administrator: Used for general configuration management related to computers and domains. This account can perform any task.
- Disable guest account.
- Change the name of the administrator account in the schema to reduce the risk of intrusion from the user of the account.
User Account Locations
Zynga Domain Poker Chip Users are created in the User Manager. When an account is created, it is automatically displayed in the primary domain controller (PDC) SAM, which then synchronizes it with the rest of the domain. This may take a few minutes. After creating an account in the actual SAM PDC, the user in many casescan log on to the domain from any computer on the workstation.
Local Users are accounts created on your own member server or on a Windows NT Workstation computer using User Manager. The map is created only in SAM, which comes from all local computers. For this reason, I would say that a user can only log on to that particular type of computer.
Scheduling New User Accounts
Account creation can be simplified by planning the organization and providing information about who needs the customer account.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

Home Folder is a personal file in which the user can store most of their files. It is used as a reporting standard for executing commands such as Save. It can be stored by the user on a local computer system or on a network server.
When creating, consider the following points:
- Storing personal folders on a web server: This makes it much easier to consider a backup backup and recovery of data of different users. Otherwise, the data files must be regularly copied to the various computers on the network where the home ring folders are stored.
- Disk space on domain controllers: Windows does not have utilities for allocating disk space (Windows 2000 does). Because if you don’t take care of keeping the folders full of official files, they can quickly take up the exact storage space on the server.
- Computer without hard drive: The user’s home folder must be on a network server.
- Home folders located directly on local computers. This improves network performance because there is less data traffic on the network and the server does not process requests all the time.
Set Your Workstation And Account Settings
You can also create workstations from which the user connects to the network. You can either allow them to access the Internet from a workstation, or you can specify one or more workstations. Using one station forUsername is one way to find a highly secure network. Indeed, a user who connects to firewood at a station that he certainly does not own will connect locally and, therefore, will likely have access to all the local resources of the machine, allowing the network administrator to control the user.
You can also set an expiration date for the user account. This option can be useful if you submit an invoice to an employee too quickly. The expiration date for your account seems to be fixed every time your contract expires.
Connection Permissions
After installing RAS (Remote Access Service), you can configure Remote Access permissions. This service allows a high-privilege user to remotely access a resource network using a telephone line (or X.25). This helps users who need access to the entire network from home or elsewhere. In fact, there are several permissionscall lines that can be configured:
- No reminder: User pays for communication costs. The system does not call back the user.
- Caller-Defined: This parameter makes the user appear as if they were being called from the server at the specific number they provided. In this case, the latter pays, in particular, the communication costs.
- Default: Allows the administrator to manage the reminder. You and they define the number from which a particular user should call the server. In certain circumstances, this option can be used not only to reduce costs, but also to increase security, since the owner must be under an exclusive phone number.
Remove And Change User Account Names
When a good account is no longer needed, it can be deleted or renamed so that other users can use it. Please note that deleting the account also removes the SID (Security IDentification).
Managing User Workspace
P When the account first logs on from a Windows NT client, a default client profile is created for that user. This profile defines things like work environment, network printer, and connections. This profile can be personalized to restrict certain elements of the desktop or tools in relation to the station displayed.
These profiles contain user-defined settings for the production environment on a Windows NT laptop. These settings are immediately saved in the Profiles folder (C: Winnt Profiles).
For logging in from clients who do not use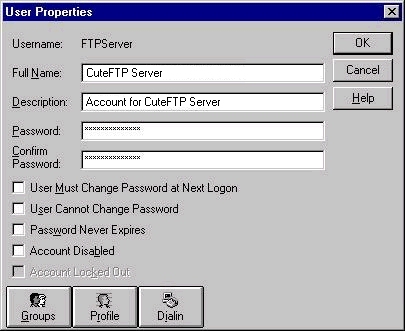
Speed up your computer's performance now with this simple download.
Windows NT could be the operating mechanism of the Microsoft Windows personal computer, designed for users and businesses that need advanced skills. Windows NT (which originally stood for New Technology, although Microsoft doesn’t say so) actually consists of two products: Microsoft NT Workstation and Microsoft NT Server.
It is a processor independent multiprocessor and therefore multiuser operating system. The first version for Windows NT was Windows NT 3.1, which was previously released for workstations and server computers. It should complement MS-DOS-based consumer versions of Windows (including Windows 1.0 – Windows 3.1x).
As part of the Microsoft Windows NT family of operating systems, a security identifier (usually abbreviated as SID) is a unique, immutable identifier created by a user, group of users, or other social security member.