Approved: Fortect
In this blog post, we will learn about some of the possible causes that can cause the vmware esxi authentication token spoofing error, and then point out possible fixes that you can try to resolve the issue. passwd: failed to manipulate authentication token For security reasons, VMware ESXi applies specific change requests. Learning how it works can prevent problems like the ones mentioned above. The length of the required security password depends on the frequency of the classes used to generate it.
No, the password must contain the username … EThis was part of * NIX to support some password complexity conventions. There is a way to more or less get rid of all the complexity of passwords, but it’s just a bad idea if this continues …
Regards, Edward L. Haletki, vmware user moderator, VMware vExpert 2009, 2010
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

– Edward L. Haletki, vExpert XIII: 2009-2021, VMTN Community Moderator
vSphere Upgrade Saga: https://www.astroarch.com/blogs
GitHub Repository: https: / / github Shouldn’t be com / texiwill
It happens, but most of the people I’ve talked to have met him at some point. You are trying to connect to your ESXi host and for other reasons your root security is no longer working.
VMware’s official position on this issue can be found in KB article 1317898, and whenever it is written it is clearly stated:
ESXi 3.5, ESXi 4.x and ESXi 5.0
Reinstallation I would say that ESXi host is the only supported system for resetting ESXi password. Any other method can lead to an outright host failure, unsupported configuration, or the complex nature of the ESXi architecture. ESXi has no technicalFrom the point of view of password reset methods, for example, when single user mode is not applied.
So, after trying and combining information from several people, I found a way to reset the exact password, but you should know that this item is not officially supported by VMware!
First of all, I recommend that you reset a lot of all running virtual machines and start them in maintenance mode. Next, go to the main screen of your vSphere client and select Host Profiles or just press Ctrl + Shift + P. Once there, create a new profile for the existing and host, especially the host that made the unknown change, and give it a name that families will remember.
Next, edit the update profile you created and open the Security Configuration section. There we select the option “Administrator password” and in the right menu “Set up a fixed manager password”.
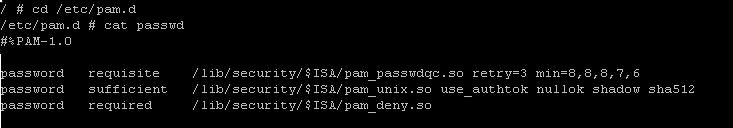
You can now set a password, but be careful with one point. You need to set the password according to a certain level Let’s take the complexity out of it. For the correct information, see VMware Understanding Base entry 1012033, which states that the specific PAM-consistent default password complexity policy is as follows:
Password required /lib/security/$ISA/pam_passwdqc.so retry = 3 min = 8,8,8,7,6 which usually means the following:
- retry = 3: user activated. It takes 3 attempts to enter the security password.
- N0 = 12: Passwords containing characters in character training class 1 must contain at least twelve cartoon characters.
Example: chars1234567 - N1 = 10: Passwords containing characters from the two character classes must be at least ten characters long.
Example: CHARs12345 - N2 = 8: Passphrases contain important content, each of which has at least eight types.
Example: software - N3 = 8: Passwords containing characters from four-character sessions must be at least eight characters long.
Example: CHARs12! - N4 = 7: Passwords containing characters from all four character classes must be at least seven characters long.
Example: CHARs1! - Example: password required/lib/security/$ISA/pam_passwdqc.so retry = 3 min = 12,10,8,8,7
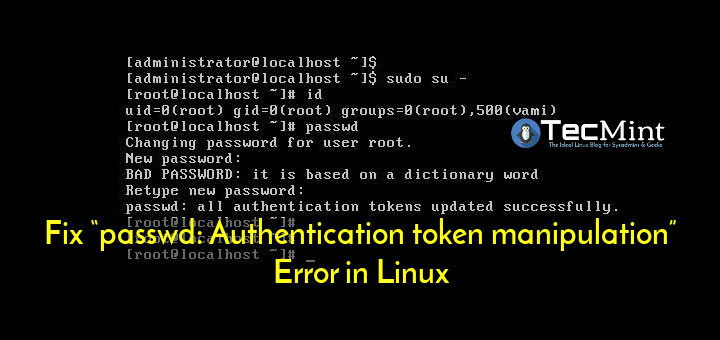
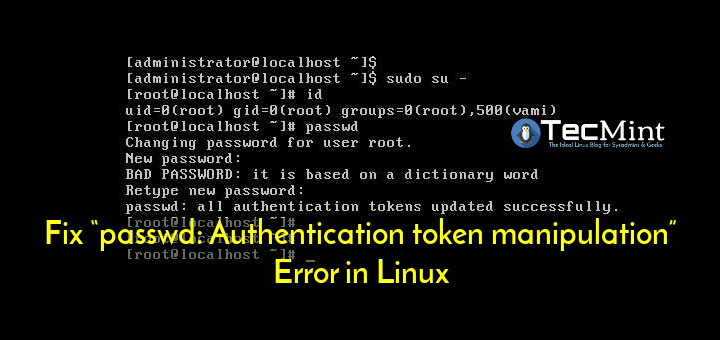
If you do not follow these rules and try to use the profile, you will receive a fatal cryptic error message which in my case only says: Authentication token method error Which is not very helpful.
Once you have set a new password, all you have to do is purchase the created profile and attach it to your host using the profile cluster view (press again on “Ctrl + Shift + H” to get to him immediate access). and right click yourself. Select Profile from the Host menu, then click Apply Profile.
The provided SSH is now disabled by the applied profile. Support it again by going to the “Configuration” tab, selecting “Security Profile” and invoking the properties of the “Services” part. You can of course start the SSH service from. You can now log in with the new shared password and it will continue to be so.
But …! There is always a “but”, isn’t there? The change only works as long as you keep the host profile or extend it, because the host remains throughout your vCenter. So what can you do to make the change permanent? Simply put, you log in with SSH, change your password with my “passwd” command, and then run the auto-backup.sh script from / sbin.
Optionally, you can also edit the following file to work around the complexity of the password you set: /etc/pam.d/passwd Go back to your own policy. If you really want to do this, create a backup associated with the change file to reflect your own policy. After that, edit the code and run the auto-backup.sh script.
Again, this is my recommendation or not VMware’s recommendation, and will affect the security of your system. So be extremely vigilant about your changes! I’m just trying to finally document the steps so you can make things a little easier if this happens.
Speed up your computer's performance now with this simple download.