Approved: Fortect
This guide will help you when you see win32 eesbinder.
This Trojan can install other adware or unwanted software on your computer.
Find out how malware can access your computer.
What To Do Now
Use the following free Microsoft software to detect and remove this threat:
- Windows Defender for Windows 10 and Windows 8.1 andMicrosoft Security Essentials for Windows 7 and Windows Vista
- Microsoft Security Scanner
You will also need to perform a full scan. A full scan can detect other hidden malware.
Get a lot of help
You can also visit our advanced troubleshooting page or seek additional help from the Microsoft Virus and / or Spyware community
If you’re using Windows XP, see our Windows XP Endpoints page for links to a support page.
EES Beam Details
-
Description
Unknown
-
Alias
Trj / W32.Drp.gen [Panda] Trojan [Panda] TrojanDropper.Win32.EESbinder [Kaspersky] Win32.TrojanRunner.EES.10 [Computer Associates] Win32 / EES.10! Trojan [Computer Associates] Win32 / EESbinder! Joiner! Dropper [Computer Associates]
-
Execution
ees binder.exeeesstub.exe
This adware enters the system in the form of data dropped by other malware, or in the form of a corresponding file that users unknowingly download when they visit websites.
Arrival Details
This spyware enters a community file that has been abandoned by other malware and a file that you unknowingly downloaded when visiting malicious websites. …
Installation
This spyware leaves the following copies on my system: affected
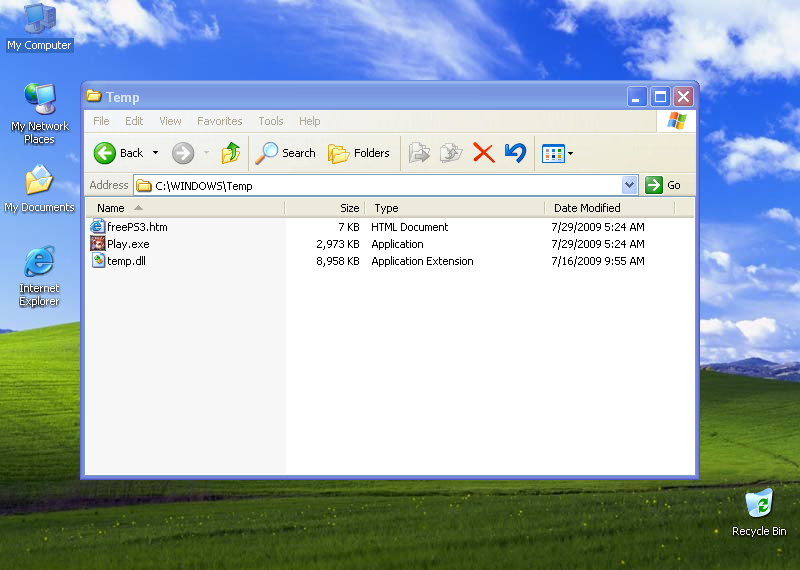
- % Temp% temp.dll
(Note:% Temp% is a type of Windows temp folder, usually C: Windows Temp.)
Other system changes
This spyware removes the following file types :
- % Temp% temp.dll
(Note:% Temp% is the temporary Windows directory, usually C: Windows Temp .)
Uninstallation Procedure
This Spywa re stores the following files:
- % Temp% 2go.jar
- % Temp% extract.exe
(Note: if% temp% is a Windows temp folder, i.e. C: Windows Temp.)
This report is generated automatically by the current analysis system.
Step 1
Before running a scan, Windows XP, Windows Vista and Windows 7 users should disable System Restore to allow full analysis of their individual computers …
Step 2
Find and remove these types of components
[Learn more]
Some components may be hidden all the time. Select the “Search for hidden files and folders” checkbox in the “Even more elegant options” option to include all hidden computers and folders in the search results.
- % Temp% 2go.jar
- % Temp% extract.exe
Step 3
Scan your computer with a Trend Micro product to remove applications identified as TSPY_KEYLO.SMUM. If tracked files have already been cleaned up, deleted or quarantined from time to time by your popular product, micro. You can easily remove files from quarantine. You can find much more information on the Knowledge Base page.
Step 4
File Restore These latest Microsoft related files from the backup will be restored. If my malware or unwanted software also deleted files related to a third-party program, reinstall those programs on your computer.
- % Temp% temp. Was this DLL description
helpful to you? Tell us how we are doing.
This spyware arrives on a schedule as a file that is removed by other adware, or as a file that users unknowingly download when they visit malicious websites.
This adware enters the system either as a computer file dropped by other malware, or as a huge file unknowingly downloaded by users who were visiting malicious websites at the time.
This spyware itself refuses to use copies in the vulnerable function:
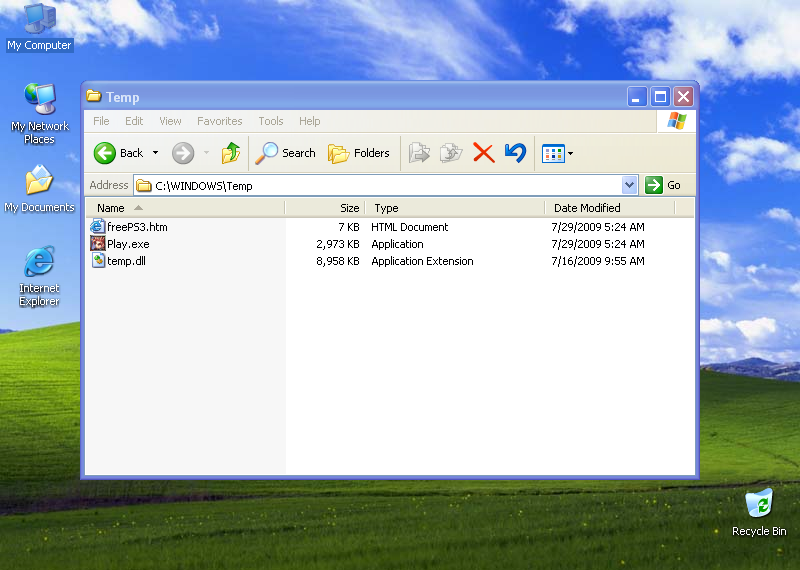
- % Temp% temp.dll
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

(Note:% Temp% is a temporary Windows file, usually C: Windows Temp.)
- % Temp% temp.dll
(Note:% Temp% is definitely a Windows temp folder, usually C: Windows Temp.)
- % Temp% 2go.jar
- % Temp% extract.exe
(Note:% Temp% is the Windows temp folder, usually also C: Windows Temp.)
Before performing a scan, Windows XP, Windows Vista and Windows 7 users should disable System Restore to allow their computers to perform a dual scan.
Some components may be hidden. Be sure to check the box “Searchhidden files and folders “in the” Advanced options “option to show all hidden files and folders in all search results.
- % Temp% 2go.jar
- % Temp% extract.exe
Scan the entire computer with Micro-Trend and remove files recognized as TSPY_KEYLO.SMUM. If the detected files have already been repaired, deleted, or quarantined using the Trend product, no further action is required. You can also just delete all quarantined files. More information is available on the search page of this database.
Restoring recorded files will only restore files associated with Microsoft. If this malware or unwanted software also deleted files associated with third-party programs, be sure to reinstall those programs on your computer.
- % Temp% temp.dll
Speed up your computer's performance now with this simple download.