Approved: Fortect
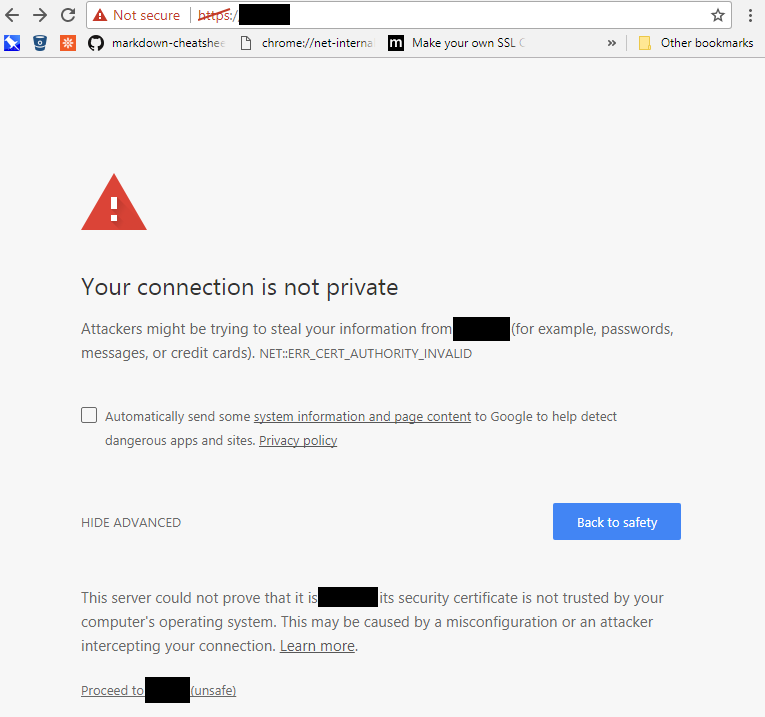
The applied connection policy (tunnel group) does not allow the certificate. The certificate may be valid for another network policy configured on the secure gateway.
is configured for secure login. This feature helps secure the private network by forcing the user to re-authenticate against the secure gateway.
Gateway for VPN session. This feature allows you to maintain the privacy of your network by asking the user to authenticate with the search gateway.

Would you go to a store that looks like a cover for illegal trade? Probably less, at least I hope not. Welcome to every 21st century where websites are virtual commerce. Most security-conscious Internet users will not visit a new website if it says “Insecure” in red. Unless you are a cybercriminal (or a hapless businessman), your target audience is likely to be more than gullible users who ignore security warnings and log into your site t. Therefore, it is in the best interest of users and website owners to use the latest reliable SSL certificate and bug fixes from bon for a safe and hassle-free shopping experience.
What Is SSL / TLS? Why Do We Use An SSL / TLS Certificate?
SSL, on the other hand, Secure Sockets Layer TLS and (Transport Layer Security) are cryptographic protocols that were designed to transfer a secure channel of communication between clients and servers on the Internet. SSL is one of the older encryption protocols, while tls is a relatively new version. The purpose of using an SSL / TLS certificate was not only to support authentication, but also to determine the type of remote server that the client browser usually communicates with. For example, let’s say the browser communicating with https://www.yourdomain.com and its SSL / TLS certificate for the website is legitimate. This indicates two things:
- The channel is usually encrypted; so that’s allEavesdropping at the end of the network may be due to truncated information that cannot beread.
- Your phone is connected to the current website andnot an impostor.
This is, of course, the intention. Fast forward to reality, and lately, about 50% of phishing websites use HTTPS to connect to spam users. The purpose of the EV SSL certificate is to thoroughly check the domain for its information. At least there is now liability as the business has to be registered and the owner has to cover the EV certificate.
SSL / TLS ensures confidentiality and data integrity. We use SSL / TLS to transfer data securely over cable. Encrypting data detected in transit helps prevent attackers from snooping on your network, stealing, and leaking sensitive information such as passwords and credit card information.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.

SSL / TLS certificates are signed by another third party called a certification authority, which prevents attackers from creating fake certificates and impersonating them as valid. The browser warns the website user who is using invalid entries (they cannot be traced back to the root certification authority or there is an incompatibility of the companies specifiedin the certificate). Is it advisable not to visit such an important website, as this could indicate that most people are directed to a phishing website, possibly a fake website.
What Does The Expiration Date Of An Invalid SSL User Certificate Mean?
- Planning your website will lose confidence due to lack of trust.
- Some users may be confident that you are hosting a good malicious website and will seek clear advice as soon as the problem is resolved. has been fixed.
- Doing business and degrading your current reputation, especially if you are not a determined gamer with a temporary technical problem.
- When SSL certificate is marked invalidthrough the respective browser, the data you exchange and the website you want to viewconnect to can be passed in clear text. Users can use almost any credentialor other sensitive data transmitted over the new channel may be snooped or stolen intermediate certificate.Certificate errors can occur if you, as the website owner, buy fromInstall the certificate online or on a CDN, but the certificate is up to date.Details are often not filled in correctly. You can use Qualys Free SSL VerificationSSL Labs who can verify the validity of the SSL certificate atWeb server.
- Certificate has been revoked or receivedillegal.
- The ERR_CERT_COMMON_NAME_INVALID error will mean that it isthis is a possible mismatch between the domain names you are trying to find andone is included in the certificate. The website owner must verify the global web address.in the correct format before the CA sends the certificate. remember, thatIn the meantime, the domain https://www.example.com will be enabled.https: // example certificate.com is actually different and cannot be registered as part of the certificate.SSL.
- Trusted certificate series is broken.(possibly because a specific root CA or some of the root / intermediate elements cannot be verifiedThe certificate has expired).
- The certificate needs to be renewed.expires before expirationExpiration of the certificate to avoid conflicts due to the violation of the era.Make sure your computer’s date and time are set correctly because they are perfectused to estimate the expiration date of all SSL certificates on the site.
- Structural tool defective orThe signature of the certificate cannot remain verified.
- It is best to obtain your degree from trusted certification authorities (CAs) such as Symantec, Thawte, Comodo, etc. to avoid browser warnings. If using a self-signed voucher, configure your domain to use full SSL instead of full SSL (strict).
- Check your antivirus or firewall protection. You may need to disable every option, such as encrypted / SSL scan or verification.
- Websites that only use SHA-1 file encryption are flagged as insecure and should help you renew their security certificates.
Invalid SSL / TLS Certificate – Security Implications
Since an invalid SSL / TLS certificate makes the communication channel between the clientand the server unencrypted, and the data is transmitted in clear text, this can lead to a serious violation of security rules. An attacker is an eavesdropping technique that allows a network to steal user credentials or session IDs for a specific session, as well as information it collects in order to impersonate legitimate users or exploit software control vulnerabilities. An invalid SSL certificate could point to a malicious website. When in doubt, it is always advised not to go to websites that are flagged as unsafe or that display animal welfare warnings.
As a website owner, brand reputation has been tarnished when some end users receive numerous warnings or error messages when visiting your website. It is indeed advisable to purchase an SSL / TLS certificate obtained from a trusted CA as they are primarily affordable and the benefits far outweigh the costs. Learn more about SSL and TLS aspects in ourx SSL resources.
Encryption Resources
- Hash versus encryption – big players in most cybersecurity worlds
- What is En
Speed up your computer's performance now with this simple download.