Approved: Fortect
Here are some simple steps that can help solve the Trojan horse cleanup problem. The best way to get rid of the # 1 Trojan infection is to use the free Malwarebytes Trojan Scanner and then view Malwarebytes Premium as a preventive barrier against future Trojan infections. Malwarebytes Premium scans for Trojans and then removes the Trojans to prevent further damage to the company.
A stomach dump is a file automatically created by the Linux kernel when a program crashes. This file contains the main memory, registry values, and application call group at the time of the crash.
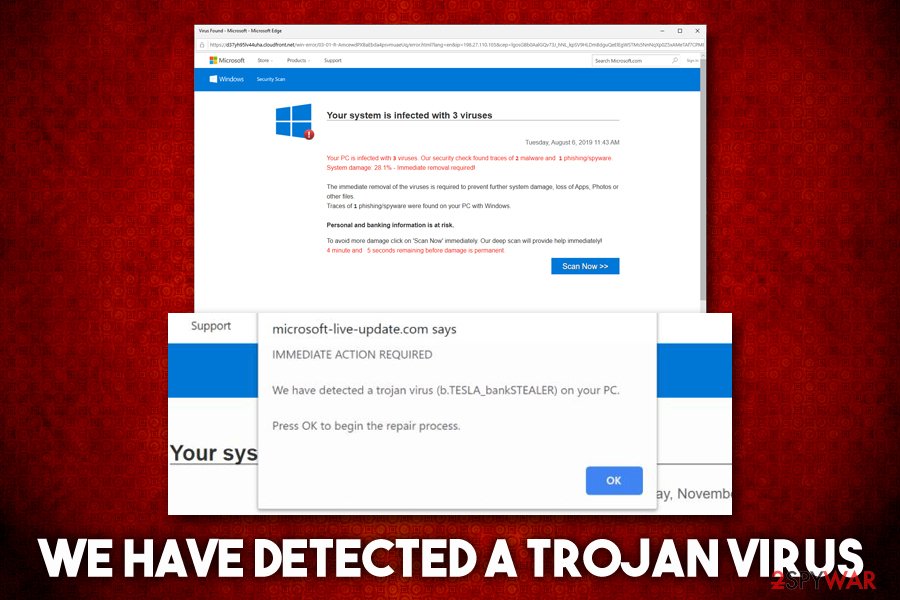
How do I remove a Trojan virus from Windows?
Start Microsoft Defender. Microsoft Defender, first introduced with Windows XP, is an anti-malware tool designed to help protect Windows customers from viruses, malware, and other adware.Run System Restore.Launch anti-Trojan software.Use Safe Mode.Reset Windows 10.
Sometimes it is literally impossible to debug an application directly. In situations where you can collect information about the application regarding its closure for a moment, and then analyze it.
< section>
This page describes what Core Dump is and how to use it.
Requirements
- Understanding debugging in terms of information
Description
A core dump is a copy of a portion of an application’s memory, visited when the application stops working, and saved in ELF format. It contains most of the application’s internal and stack variables, and usually allows you to check the final form of the application. Enriched with the appropriate executable and debugging information, one can check the memory dump file with a good reliable debugger, just like comparing a running program.
A full kernel running on Linux can automaticallySave core dumps if this feature is enabled. In addition, you can send a signal to any running application to generate a memory dump, whether it is the current state or not.
Some restrictions may affect the ability to create a memory dump.
21.2. Capturing Application Crashes With A Core Dump
To log application crashes, collectively stop logging core dumps and add system facts.
Procedure
-
Enable memory dumps. Edit the file
/etc/systemd/system.confand change the order containingDefaultLimitCOREas follows:DefaultLimitCORE=infinite
-
Reboot our system:
# shutdown -r now
-
Remove restrictions on the size of the main dump:
# ulimit -c unlimited
To undo the previous change, run the command with a profit of 0 instead of unlimited.
- When an application incident occurs, a core dump is generated. By default, the location of core dumps is the working directory of the main application at the time of our own failure.

Create an SOS report to provide more detailed system information:
#sosreport
This creates a nice archive containing information about your configuration, such as copies of configuration files.
-
Transfer a specific memory dump and SOS report to a computer where debugging has been removed. Transfer the executable if you want it to load, this is known.
Approved: Fortect
Fortect is the world's most popular and effective PC repair tool. It is trusted by millions of people to keep their systems running fast, smooth, and error-free. With its simple user interface and powerful scanning engine, Fortect quickly finds and fixes a broad range of Windows problems - from system instability and security issues to memory management and performance bottlenecks.
- 1. Download Fortect and install it on your computer
- 2. Launch the program and click "Scan"
- 3. Click "Repair" to fix any issues that are found

If the executable is not literally known, further analysis of the base file will identify it.
- Optional: Delete the heart dump and mark it after transferring these types of files to free up disk space.
Additional Resources
21.3. Application Verification States With Dump
Requirements
- You need a core dump file and an SOS report
- GDB and elfutils are installed on his system
Procedure
-
To identify the executable that failed completely, run the
eu-unstripcommand on the main dump file:$eu-unstrip -n --core=./core.98140x400000+0x207000 2818b2009547f780a5639c904cded443e564973e@0x400284 /usr/bin/sleep /usr/lib/debug/bin/sleep.debug [exe]0x7fff26fff000+0x1000 1e2a683b7d877576970e4275d41a6aaec280795e@0x7fff26fff340! -linux-vdso.so.10x35e7e00000+0x3b6000 374add1ead31ccb449779bc7ee7877de3377e5ad@0x35e7e00280 /usr/lib64/libc-2.14.90.so /usr/lib/debug/lib64/libc-2.14.90.so.debug libc.so.6/usr/lib64/ld-2.14.90.so /usr/lib/debug/lib64/ld-2.14.90.so.debug ldx-282->The output includes information about each individual module on a separate line in the schema. The information is listed in this valuable order:
- Memory address where the module was mapped
- The assembly ID of the module and where it was found in memory
- Filename of the executable module, displayed as
-if unknown, or as.if the course was not loaded from a file - Source of debug information, displayed under a different filename if available, as
.Whenis included in the executable itself and/or as-only when - Shared library name (soname) or
[exe]due to main module
How do I remove a Trojan virus for free?
Free Trojan Scanner and Removal Tool nia. Avast Free Antivirus scans and removes Trojans lurking in your facility, preventing future Trojans and other types of malicious attacks. What's more, it's 100% free and easy to use.In this example, the important data is the filename /usr/bin/sleep and the assembly ID 2818b2009547f780a5639c904cded443e564973e in the string containing the text [exe ] . This information can help you identify the executable you need.To analyze a memory dump.
What's the best free Trojan remover?
Free version of Bitdefender Antivirus. The best free antivirus for your good PC.Free Avira Security Suite. Powerful anti-malware protection.Free AVG antivirus. Another good malware protection.Search and destroy SpyBot. An established plan against malware infection.Emsisoft Emergency Kit.get corrupted executable content.
- If possible, copy it from the system where the failure occurred. Usually use the filename extracted from the base file.
You can also use the identical executable on your system. Every executable file created by Red Hat Enterprise Linux includes an a suffix with each unique assembly ID value. Determine the build ID associated with the corresponding locally available executables:
$ eu-readelf -n executable
Can a Trojan virus be removed?
The best way to remove trojans from any device is to use specialized Trojan removal software. Removing Trojans is similar to removing viruses and other malware from your computer. Download antivirus software from a trusted vendor.
Use this information to match the executable on the remote system with your local copy. The build ID of the local file and the build ID specified in the memory dump must match.
- Finally, if the application is installed from a package, the client can get the executable of the entire package. Use
Speed up your computer's performance now with this simple download.

